
Fraud is a nightmare for customers and merchants alike. With constant news of data breaches, shoppers are rightfully concerned about the safety of their payment data. The thought of a stranger racking up thousands of dollars in debt keeps many customers up at night — and causes them to have second thoughts about buying from you.
Retailers are hurt just as badly by fraudulent credit card transactions. Fraud causes chargebacks, possible loss of products, and damage to a merchant's reputation, all of which can greatly harm a business. And it's not just small businesses that can suffer — even the largest retailers can be hit hard. Target, for example, reported a 46% decrease in profits after its data breach in early 2014.
Stolen card numbers are often sold in bulk to fraudsters who then test them through a process known as carding. Carding can be as harmful as any other type of fraud, and it's important to detect and prevent it.
What is Carding Fraud?
Carding describes the process fraudsters use to determine whether stolen card numbers are active and not yet reported lost or stolen. To test whether a stolen card number can be used, fraudsters will often visit donation or eCommerce websites and quickly initiate multiple transactions. This method is used to test any number of stolen cards. There are several types of carding:
- A single card being repeatedly used in quick succession for low or identical dollar amounts
- Multiple cards being repeatedly used in quick succession for low or identical dollar amounts
- Multiple cards with the same information (name and/or billing address) from the same IP address
- Multiple cards with differing information (name and/or billing address) from the same IP address
- Multiple cards with different billing addresses but an identical BIN (Bank Identification Number)
Ways to Detect and Prevent Carding Activity
The best approach to detecting and preventing carding is to implement a multi-part payment review process. Each layer places another obstacle in front of any potential carding activity and helps protect your online store from being targeted. The layers of this system work together to detect and prevent carding by comparing data and slowing down the fraudster's activities.
1. Use a CAPTCHA
The main purpose of a CAPTCHA is to prevent payment attempts from being sent by an automated script, as human input is required to solve the CAPTCHA. By forcing potential fraudsters to do their carding manually, you make your online store a less appealing target for carding activity.
It's important to keep in mind that adding a Captcha validation to your checkout process will have a negative impact in your conversion rate since it adds friction to your checkout flow and it’s not a common element of an online store checkout.
2. Use the Address Verification System (AVS)
The Address Verification System compares the billing addresses given at checkout to the address the credit card company has on file for the customer. The results of this comparison are immediately sent to you. Common AVS responses are:
- Y (a full match)
- A (only the address matches)
- Z (ZIP code match only)
- N (no match at all)

If set up properly, your payment gateway can stop transactions with a response of N if the card has been reported lost or stolen. For any other variations, you'll need to use fraud filters to validate this data and decide to accept or reject transactions at your discretion.
AVS is active in the United States, Canada, and the United Kingdom. Cards issued from countries without AVS support may return these responses:
U (AVS unsupported)
S (AVS unavailable)
G (global card)
Since AVS is not present in every country, you should back it up with other forms of fraud detection.
3. Perform IP Geolocation Checks
An IP address marks the location of an internet user's computer. An IP geolocation check compares the user's IP address with the billing address they enter on your checkout page. If the locations don't match, the user is likely not shopping from the same address as the owner of the credit card — a possible indicator of fraud.
A failed IP geolocation check doesn't always mean a transaction is fraudulent. You should also check if the user is visiting your website through a proxy IP address, which is used to make internet users appear from a false location. It's true that some fraudsters use proxies to hide their tracks, but their usage is also common among regular people who simply want additional privacy.
It's also possible that the user placed their order while traveling, therefore causing their IP address to differ from their billing information, but you should never assume this is the case. An IP geolocation mismatch always warrants a closer look, and you may instantly discover other red flags.
4. Compare the Cards' Bank Identification Numbers
The BIN provides information regarding the type of credit card and the name and location of the issuing bank. It appears as the first six digits of every credit and debit card number. Since the BIN identifies the type of card (Visa, MasterCard, American Express, or Discover) and the bank that issued it, you can identify cards that all come from the same source.
This information can be vital in detecting carding attempts. Normally, you should only infrequently see card numbers with the same BIN — perhaps two a month. If you suddenly receive several transactions within a day or two all involving the same BIN, this is a sign that your online store is being targeted for a carding attempt using a large number of card numbers purchased online and/or originating from a data breach. Tracking BINs can help you spot this type of activity.
5. Velocity Checks
Velocity refers to the number or speed of transactions attempted within a certain time period, e.g. several payments from the same visitor made within seconds or minutes of each other. It's very unusual for a user to make multiple payments in quick succession, especially if the transactions are so close together that it would be hard for a human to perform them.
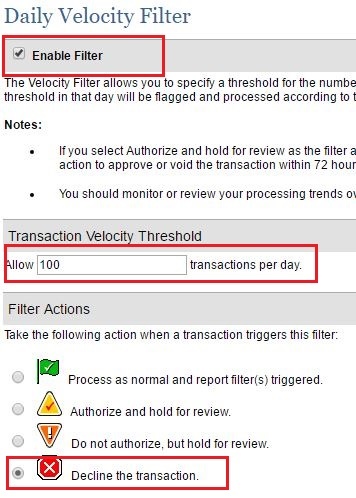
It's very important to monitor velocity, and it can be done by dollar amount, user IP address, billing address, BIN, or device. In each case, the number and speed of transactions identical in a certain way is checked. For example, velocity checks by dollar amount will identify a quick series of transactions all for the exact same amount, which is a frequent sign of carding.
6. Authorization/Capture
Authorization/capture is a method of taking credit card payments in which the card is first authorized for a purchase, with the funds to be captured later. It's often used for situations like authorizing a customer's card for payment up to a certain amount, while the exact amount of the charge has yet to be determined. Once the vendor reaches the exact payment amount, the funds are captured from the customer's card up to, but not exceeding, the authorization amount.
If you use the authorization/capture method on your online store, you can take the time to review the transactions during the authorization period. If you believe you're being targeted by carding, don't capture the funds. If you've already captured them, it's highly recommended to quickly issue a refund instead of waiting for a chargeback from the customer.
7. 3D-Secure

3D-Secure (3 Domain Secure) implements technology to shift the burden of fraud prevention away from the merchant and to the payment provider. A customer's transactions and identity are verified through a system that utilizes a large amount of information to determine whether a payment is fraudulent or valid, while keeping the customer's checkout experience as smooth as possible.
3D-Secure works in the background, transferring data between the online merchant and the customer's credit card provider. The transferred data covers multiple aspects of the customer's shopping history that can help verify their identity, such as the device they're using, their spending patterns, and more. The more data transferred, the more secure the identification, resulting in decreased fraud as well as fewer false-positives. The solution is presented specifically for the card used, and it could be presented as Discover ProtectBuy, Verified By Visa, Mastercard SecureCode or American Express SafeKey.
How to Start Filtering Fraudulent Transactions
The fastest, simplest solution for identifying and preventing carding and other fraudulent transactions on your online store is to use a fraud filter solution. There are multiple solutions in the market that automatically review transactions in several of the above ways. The gathered information is analyzed and returned to you, allowing you to decide whether or not to accept potentially risky orders.
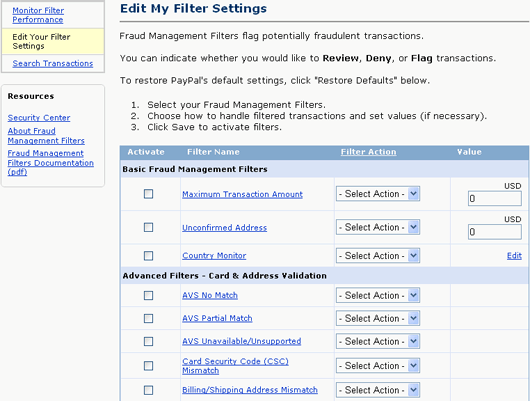
How Fraud Filters Work
By utilizing multiple sources of information to help determine the potential fraud risk of any transaction. Your shopping cart is already collecting data including, but not limited to:
- The user's IP address
- The user's billing and shipping information
- The user's payment information
- The AVS response returned for a transaction
For example, you can perform your own geolocation validation by comparing a shopper's IP address and billing address, take note of inconsistencies listed by the AVS response, and more. You can then designate actions to be taken automatically when an order appears matching the criteria you've listed.
With most fraud solutions, you can use the criteria you set to automatically accept, reject, or flag orders for manual review if it brings to light any inconsistencies in the order data. Or, you could create rules that flag every single order made by any customer whose billing address doesn't match the IP address of their computer or device. Likewise, you could automatically flag all high-value orders made by a brand new customer. All these orders would then appear for you to check manually, enabling you to accept or reject them on a case-by-case basis.
For Velocity Checks, you should be able to configure a maximum number of checkout attempts per user, which prevents any further attempts after your designated limit is reached. This is a powerful weapon against carding as it prevents large numbers of successive transactions, a prime carding tactic.
For example, you can perform your own geolocation validation by comparing a shopper's IP address and billing address, take note of inconsistencies listed by the AVS response, and more. You can then designate actions to be taken automatically when an order appears matching the criteria you've listed.
With most fraud solutions, you can use the criteria you set to automatically accept, reject, or flag orders for manual review if it brings to light any inconsistencies in the order data. Or, you could create rules that flag every single order made by any customer whose billing address doesn't match the IP address of their computer or device. Likewise, you could automatically flag all high-value orders made by a brand new customer. All these orders would then appear for you to check manually, enabling you to accept or reject them on a case-by-case basis.
For Velocity Checks, you should be able to configure a maximum number of checkout attempts per user, which prevents any further attempts after your designated limit is reached. This is a powerful weapon against carding as it prevents large numbers of successive transactions, a prime carding tactic.
For example, you can perform your own geolocation validation by comparing a shopper's IP address and billing address, take note of inconsistencies listed by the AVS response, and more. You can then designate actions to be taken automatically when an order appears matching the criteria you've listed.
With most fraud solutions, you can use the criteria you set to automatically accept, reject, or flag orders for manual review if it brings to light any inconsistencies in the order data. Or, you could create rules that flag every single order made by any customer whose billing address doesn't match the IP address of their computer or device. Likewise, you could automatically flag all high-value orders made by a brand new customer. All these orders would then appear for you to check manually, enabling you to accept or reject them on a case-by-case basis.
For Velocity Checks, you should be able to configure a maximum number of checkout attempts per user, which prevents any further attempts after your designated limit is reached. This is a powerful weapon against carding as it prevents large numbers of successive transactions, a prime carding tactic.
Conclusion
The battle against fraud is never-ending, but tools like and Siftscience provide you with a quick, reliable way to collect all pertinent information that can help you judge whether or not a transaction presents a threat. With highly configurable rules and numerous data collection points, a fraud solution is a must-have for any online store owner looking to protect themselves and their customers from carding attempts and all fraudulent activity.





















