Indeed, attacks on Web applications and on the application layer in general are plentiful. Protecting against these types of attacks is particularly challenging since many are zero-day exploits caused by software bugs or Web server misconfiguration. Application security is a complex problem. You can’t just put a firewall in front of your organization’s critical infrastructure and hope for the best , Website, attacks involving Web applications and websites were responsible for the majority of security issues recorded in 2014.
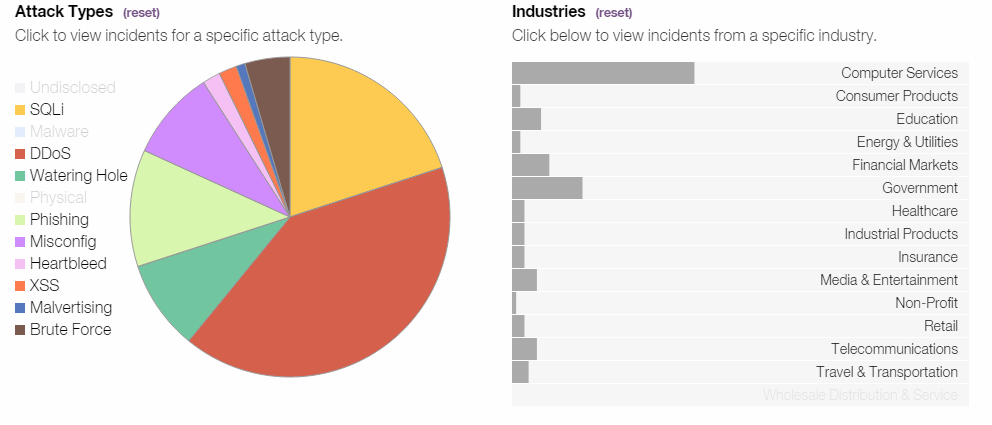
The following snapshot was taken from the page linked above:
Special Security Considerations for Mobile Applications
Besides Web applications, there is a booming mobile sector with millions of mobile applications and billions of mobile devices. How many of these applications are designed with security in mind? Not as many as you might think!
In a previous blog, I discussed how software defenses implemented early in the development stage represent the best approach to preventing software vulnerabilities. To stay protected, organizations must undertake the enormous task of chasing security defects in their software and educating developers to prevent such defects from recurring. But how does an organization accomplish that?
Imagine that you are running a website with millions of lines of code, with hundreds of projects and thousands of developers. Finding an SQL injection in such a site sounds like finding a proverbial needle in a haystack. And yet attackers still come across them one way or another. Attackers execute hundreds of probes every hour from many locations across the globe, which sweep the Internet and attempt to poke holes into your public applications. To see a visual representation of these attacks, visit the IBM X-Force Exchange.
Let’s say you found a potential SQL injection vulnerability before the attackers did. How do you go about fixing it? How do you deploy patches and monitor the security issue until it’s fixed to completion? How do you retest?
I lead the Security Incident Response efforts for an organization that offers more than 100 products to its customer base. Believe me, patching security defects is not a walk in the park. Companies must follow a defined application security program that covers several aspects and initiatives, which are recapped below:
Education
Educating developers about security threats is the first step. If developers have an understanding of basic attacks, then they can develop code securely. Organizations must put together training that documents secure coding practices and security initiatives. The Open Web Application Security Project (OWASP) stores a wealth of information for developers and security testers to expand their knowledge base.
Threat Modeling and Secure Coding
Designing software defenses even before the code is written can save organizations millions of dollars. The “2014 Cost of Data Breach Study” by the Ponemon Institute estimated that the average total cost of a security breach was $3.5 million for companies that participated in its research. What is the cost of implementing a software defense such as input validation from the moment the code is written? Would you say $100? Maybe even less?
Threat modeling is an exercise that developers can undertake to understand countermeasures that need to be taken at the software level to prevent security threats. Secure coding is abiding by these countermeasures in the implementation stage.
CURIOUS ABOUT APPLICATION SECURITY? JOIN THE IBM TEAM FOR A REDDIT ‘ASK ME ANYTHING’ (AMA) ON MAY 13
Application Security Testing
How do you test that the code is written securely, and how do you test that the designed software defenses work as they’re expected to?
Static analysis is a technology that performs automated security code reviews and verifies that your code has been written securely. These tools can even be integrated with software build systems to run in an automated fashion and trigger alerts.
I mentioned earlier that cybercriminals test public applications with hundreds of probes each hour. Organizations must employ their own white-hat hackers to do the same. Penetration testing is the act of simulating real-life attacks with the purpose of securing an organization. My team conducts penetration testing for IBM Security’s offerings.
Application security testing tools can execute thousands of attack variants in a matter of hours, including identifying issues in third-party components or within your application infrastructure. They represent a valuable tool for penetration testers and quality assurance engineers to learn about potential “holes” in your security preparedness. Application security scanners can also be integrated with QA automation scripts.
Monitoring and Managing Application Security Activities
The activities I previously described must be monitored through a centralized system. I have used spreadsheets in the past, and I can tell you that your system should not be based on primitive spreadsheets. It should be centered on a secure collaboration platform where developers and security experts can meet. This system offers you the ability to calculate risk, prioritize various secure engineering activities and monitor security issues coming from various sources.
Conclusion
Securing Web applications is not just a matter of writing secure code. Organizations large and small must establish a well-defined application security testing program that includes their entire application portfolio. This program must touch on various areas including education, threat modeling, secure coding, application security testing and incident response.
The following snapshot was taken from the page linked above:
Special Security Considerations for Mobile Applications
Besides Web applications, there is a booming mobile sector with millions of mobile applications and billions of mobile devices. How many of these applications are designed with security in mind? Not as many as you might think!
In a previous blog, I discussed how software defenses implemented early in the development stage represent the best approach to preventing software vulnerabilities. To stay protected, organizations must undertake the enormous task of chasing security defects in their software and educating developers to prevent such defects from recurring. But how does an organization accomplish that?
Imagine that you are running a website with millions of lines of code, with hundreds of projects and thousands of developers. Finding an SQL injection in such a site sounds like finding a proverbial needle in a haystack. And yet attackers still come across them one way or another. Attackers execute hundreds of probes every hour from many locations across the globe, which sweep the Internet and attempt to poke holes into your public applications. To see a visual representation of these attacks, visit the IBM X-Force Exchange.
Let’s say you found a potential SQL injection vulnerability before the attackers did. How do you go about fixing it? How do you deploy patches and monitor the security issue until it’s fixed to completion? How do you retest?
I lead the Security Incident Response efforts for an organization that offers more than 100 products to its customer base. Believe me, patching security defects is not a walk in the park. Companies must follow a defined application security program that covers several aspects and initiatives, which are recapped below:
Education
Educating developers about security threats is the first step. If developers have an understanding of basic attacks, then they can develop code securely. Organizations must put together training that documents secure coding practices and security initiatives. The Open Web Application Security Project (OWASP) stores a wealth of information for developers and security testers to expand their knowledge base.
Threat Modeling and Secure Coding
Designing software defenses even before the code is written can save organizations millions of dollars. The “2014 Cost of Data Breach Study” by the Ponemon Institute estimated that the average total cost of a security breach was $3.5 million for companies that participated in its research. What is the cost of implementing a software defense such as input validation from the moment the code is written? Would you say $100? Maybe even less?
Threat modeling is an exercise that developers can undertake to understand countermeasures that need to be taken at the software level to prevent security threats. Secure coding is abiding by these countermeasures in the implementation stage.
CURIOUS ABOUT APPLICATION SECURITY? JOIN THE IBM TEAM FOR A REDDIT ‘ASK ME ANYTHING’ (AMA) ON MAY 13
Application Security Testing
How do you test that the code is written securely, and how do you test that the designed software defenses work as they’re expected to?
Static analysis is a technology that performs automated security code reviews and verifies that your code has been written securely. These tools can even be integrated with software build systems to run in an automated fashion and trigger alerts.
I mentioned earlier that cybercriminals test public applications with hundreds of probes each hour. Organizations must employ their own white-hat hackers to do the same. Penetration testing is the act of simulating real-life attacks with the purpose of securing an organization. My team conducts penetration testing for IBM Security’s offerings.
Application security testing tools can execute thousands of attack variants in a matter of hours, including identifying issues in third-party components or within your application infrastructure. They represent a valuable tool for penetration testers and quality assurance engineers to learn about potential “holes” in your security preparedness. Application security scanners can also be integrated with QA automation scripts.
Monitoring and Managing Application Security Activities
The activities I previously described must be monitored through a centralized system. I have used spreadsheets in the past, and I can tell you that your system should not be based on primitive spreadsheets. It should be centered on a secure collaboration platform where developers and security experts can meet. This system offers you the ability to calculate risk, prioritize various secure engineering activities and monitor security issues coming from various sources.
Conclusion
Securing Web applications is not just a matter of writing secure code. Organizations large and small must establish a well-defined application security testing program that includes their entire application portfolio. This program must touch on various areas including education, threat modeling, secure coding, application security testing and incident response.

















