A single administrator error can affect the entire corporate network.
The Israeli cybersecurity company Sygnia notes that virtualization platforms such as VMware ESXi often suffer from incorrect settings and vulnerabilities, which makes them attractive targets for hackers.
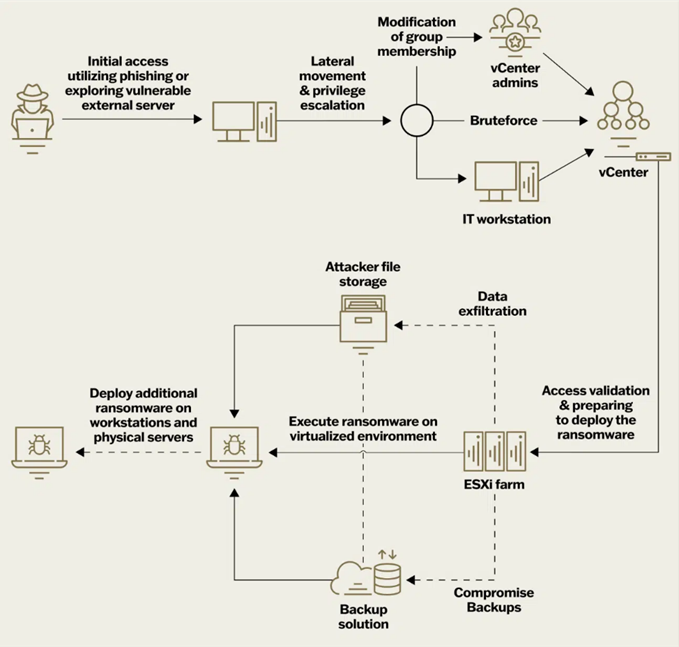
In the course of investigations related to various ransomware families, such as LockBit, HelloKitty, BlackMatter, and others, Sygnia found that attacks on virtualization environments follow a set sequence of actions:
Attack Chain
How to protect yourself
To minimize risks, organizations should ensure proper monitoring and logging, establish reliable backup mechanisms, implement strong authentication measures, strengthen infrastructure, and limit network activity to prevent intra-network movement.
The Israeli cybersecurity company Sygnia notes that virtualization platforms such as VMware ESXi often suffer from incorrect settings and vulnerabilities, which makes them attractive targets for hackers.
In the course of investigations related to various ransomware families, such as LockBit, HelloKitty, BlackMatter, and others, Sygnia found that attacks on virtualization environments follow a set sequence of actions:
- Gaining initial access: Attackers use phishing attacks, downloading malicious files, and exploiting known vulnerabilities in systems accessible from the Internet.
- Privilege escalation: Attackers gain access to credentials for ESXi or vCenter hosts using various methods, including brute-force attacks.
- Access verification: Cybercriminals check access to the virtualization infrastructure and implement ransomware.
- Deleting or encrypting backups: To complicate the recovery process, backups are either deleted or encrypted, and sometimes passwords are changed.
- Data exfiltration: Data is sent to external resources, such as Mega.io, Dropbox, or the attackers own hosting services.
- Starting the ransomware: Encryption of the "/vmfs/volumes" folder in the ESXi file system begins.
- Ransomware distribution: Ransomware is distributed to "non-virtualized" servers and workstations to expand the attack zone.

Attack Chain
How to protect yourself
To minimize risks, organizations should ensure proper monitoring and logging, establish reliable backup mechanisms, implement strong authentication measures, strengthen infrastructure, and limit network activity to prevent intra-network movement.














