Article content
Looking for files
Filtering the search results
We use bureaucracy
Climbing into the clouds
Spying on configs
Reveal passwords from the database
Don't forget the obvious
Keep an eye out for updates
Targeting and filtering again
Finally, an example
Getting private data does not always mean hacking - sometimes it is published in the public domain. Knowledge of Google settings and a little ingenuity will allow you to find a lot of interesting things-from credit card numbers to FBI documents.
WARNING
All information is provided for informational purposes only. The author are responsible for any possible damage caused by the materials of this article.
Everyone is connected to the Internet today, not caring much about restricting access. Therefore, many private data become the prey of search engines. Spider robots no longer limit themselves to web pages, but index all the content available on the Web and constantly add information that is not intended for disclosure to their databases. It's easy to learn these secrets - you just need to know how to ask about them.
Looking for files
In the right hands, Google will quickly find everything that is bad on the Web - such as personal information and files for official use. They are often hidden like a key under a rug: there are no real access restrictions, the data just lies in the back of the site, where links do not lead. Google's standard web interface provides only basic advanced search settings, but even that will be enough.
You can restrict the search for certain types of files in Google by using two operators: filetypeand ext. The first one sets the format that the search engine determined by the file header, and the second one sets the file extension, regardless of its internal content. When searching in both cases, you only need to specify the extension. Initially, the operator ext it was convenient to use it in cases where there were no specific features of the file format (for example, to search for ini and cfg configuration files, which can contain anything). Now Google's algorithms have changed, and there is no visible difference between the operators — the results in most cases are the same.
Search results with filetype and ext are now the same Search results with filetype and ext are now the same
WWW
Examples of using advanced search operators in Google
Updated selection of Google dorks
Filtering the search results
By default, Google searches all files on indexed pages for words and any characters you enter. You can limit the search area by top-level domain, specific site, or by the location of the search sequence in the files themselves. For the first two options, the site statement is used, followed by the name of the domain or selected site. In the third case, a whole set of operators allows you to search for information in service fields and metadata. For example, allinurlit will find what is specified in the body of the links allinanchorthemselves - in the tagged text<a name>, allintitlein page headers, allintextand in the body of pages.
For each operator, there is a lightweight version with a shorter name (without the prefix all). The difference is that allinurlit will find links with all the words, but inurlonly with the first one. The second and subsequent words from the query can occur anywhere on web pages. The operator inurlalso has differences from another similar meaning - site. The first one also allows you to find any sequence of characters in the link to the desired document (for example, /cgi-bin/), which is widely used to search for components with known vulnerabilities.
Let's try it in practice. We take the filter allintextand make sure that the request returns a list of credit card numbers and verification codes that will expire only in two years (or when their owners get tired of feeding everyone in a row).
Code:
allintext: card number expiration date /2017 cvv
275 thousand actual credit cards, fakes and honeypots for freebie lovers
When you read in the news that a young hacker "hacked the servers" of the Pentagon or NASA, stealing classified information, then in most cases we are talking about this elementary technique of using Google. Suppose we are interested in a list of NASA employees and their contact details. Surely such a list is available in electronic form. For convenience or due to an oversight, it may also be located on the organization's website itself. It is logical that in this case it will not be referenced, since it is intended for internal use. What words can be in such a file? At least - the "address" field. Check out all of these simple assumptions.
Using two operators, you can get "secret" NASA documents in 0.36 seconds
We write
Code:
inurl:nasa.gov filetype:xlsx "address"
and we get links to files with lists of employees.
Addresses and phone numbers of key NASA employees in an Excel file
We use bureaucracy
Such findings are a pleasant trifle. A truly solid catch is provided by a more detailed knowledge of Google operators for webmasters, the Network itself, and the structure of the search engine. Knowing the details, you can easily filter the output and Refine the properties of the necessary files to get really valuable data in the balance. It's funny that bureaucracy comes to the rescue here. It produces standard formulations that make it convenient to search for secret information that has accidentally leaked to the Network.
For example, the Distribution statement stamp required by the office of the United States Department of defense means standardized restrictions on the distribution of a document. The letter A indicates public releases that do not contain anything secret; B - intended only for internal use, C - strictly confidential, and so on up to F. Separately, there is the letter X, which marks particularly valuable information that represents a state secret of the highest level. Let those who are supposed to do it on duty look for such documents, and we will limit ourselves to files with the letter C. According to the DoDI Directive 5230.24, this marking is assigned to documents containing descriptions of critical technologies that fall under export control. You can find such carefully protected information on sites in the .mil top-level domain allocated to the US army.
Code:
"DISTRIBUTION STATEMENT C" inurl:navy.mil

Example of a stamp in a security level C document
It is very convenient that in the domain .mil contains only sites from the US Department of defense and its contract organizations. Search results with domain restrictions are exceptionally clean, and the headlines speak for themselves. It is almost useless to search for Russian secrets in this way: in the domains. ru and .the Russian Federation is in chaos, and the names of many weapons systems sound like Botanical (PP "Cypress", ACS "acacia") or even fabulous (CBT "Pinocchio").
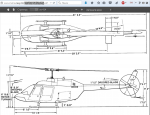
Drawing from the manual for the combat training helicopter TH-57C Sea Ranger
After carefully studying any document from the site in the .mil domain, you can see other markers to Refine the search. For example, a reference to the export restrictions "Sec 2751", which is also convenient to search for interesting technical information. From time to time, it is removed from official sites where it once appeared, so if you can't click on an interesting link in the search results, use The Google cache (cache operator) or the Internet Archive site.
Climbing into the clouds
In addition to accidentally declassified government documents, links to personal files from Dropbox and other data storage services sometimes pop up in Google's cache, which create "private" links to publicly published data. Alternative and self-made services are even worse. For example, the following query finds data from all Verizon customers who have an FTP server installed on their router and are actively using it.
Code:
allinurl:ftp:// verizon.net
There are now more than forty thousand such smart guys, and in the spring of 2015 there were an order of magnitude more of them. InsteadVerizon.net, you can substitute the name of any known provider, and the more famous it is, the bigger the catch may be. The built-in FTP server lets you view files on an external storage device connected to the router. Usually this is a NAS for remote work, a personal cloud, or some kind of peer-to-peer file rocker. All the contents of such media are indexed by Google and other search engines, so you can access files stored on external disks by using a direct link.
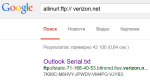
Serial numbers, documents, and forty thousand more files from private clouds
Spying on configs
Before the mass migration to the cloud, simple FTP servers were used as remote repositories, which also had enough vulnerabilities. Many of them are still relevant today. For example, the popular WS_FTP Professional program stores configuration data, user accounts, and passwords in a file ws_ftp.ini. It is easy to find and read, since all entries are saved in text format, and passwords are encrypted using the Triple DES algorithm after minimal obfuscation. In most versions, just discard the first byte.
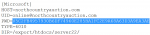
One of the ws_ftp.ini files is publicly available
It is easy to decrypt such passwords using the WS_FTP Password Decryptor utility or a free web service.
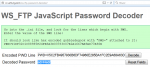
Decrypting the password takes about a second
When talking about hacking an arbitrary site, they usually mean getting a password from logs and backups of CMS configuration files or e-Commerce applications. If you know their typical structure, you can easily specify keywords. Strings like those found in ws_ftp.iniare extremely common. For example, Drupal and PrestaShop must have a user ID (UID) and a corresponding password (pwd), and all information is stored in files with the .inc extension. You can search for them in the following way:
Code:
"pwd=" "UID=" ext:inc
Reveal passwords from the database
In the configuration files of SQL servers, users ' names and email addresses are stored in clear text, and their MD5 hashes are written instead of passwords. Strictly speaking, it is impossible to decrypt them, but you can find a match among the known hash-password pairs.
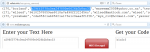
Selecting a password based on the MD5 hash
Until now, there are DBMSs that do not even use password hashing. You can simply view the configuration files of any of them in the browser.
Code:
intextB_PASSWORD filetype:env
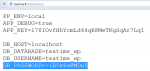
The database password is openly stored in the configuration file
With the advent of Windows servers, the registry partially took the place of configuration files. You can search through its branches in the same way, using reg as the file type. For example, like this:
Code:
filetype:reg HKEY_CURRENT_USER "Password"=
The servers with the Windows open
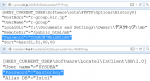
Don't forget the obvious
Sometimes it is possible to get to private information using data that is accidentally opened and caught in the field of view of Google. The ideal option is to find a list of passwords in some common format. Only desperate people can store account information in a text file, Word document, or Excel spreadsheet, but there are always enough of them.
Code:
filetype:xls inurlassword
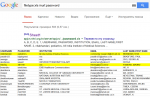
Li denghui national research Institute of health accidentally revealed a list of passwords
On the one hand, there are a lot of tools to prevent such incidents. You must specify adequate access rights in htaccess, patch the CMS, do not use left-hand scripts, and close other holes. There is also a file with a list of exceptions robots.txt, which prohibits search engines from indexing the files and directories specified in it. On the other hand, if the structure robots.txt if it differs from the standard one on some server, then you can immediately see what they are trying to hide on it.
White house welcomes robots White house welcomes robots
The list of directories and files on any site is preceded by the standard index of label. Since it must appear in the header for official purposes, it makes sense to limit its search to the operator intitle. Interesting things can be found in the /admin/, /personal/, /etc/, and even /secret/directories.
Goolge helps you get to the root of the directory list
Keep an eye out for updates
There are so many leaky systems today that the problem is no longer finding one of them, but choosing the most interesting ones (to study and improve your own security, of course). Examples of search queries that reveal someone's secrets are called Google dorks. One of the first utilities to automatically check the security of sites based on known Google queries was McAfee SiteDigger, but its latest version was released in 2009. Now there are a lot of other tools available to simplify the search for vulnerabilities. For example, SearchDiggity by Bishop Fox, as well as top-UPS databases with a selection of current examples.
Relevance here is extremely important: old vulnerabilities are closed very slowly, but Google and its search results are constantly changing. There is even a difference between the filter "last second" (&tbs=qdr:s at the end of the request url) and "real-time" (&tbs=qdr:1).
The time interval of the last file update date is also specified implicitly by Google. You can use the graphical web interface to select one of the standard periods (hour, day, week, and so on) or set a date range, but this method is not suitable for automation.
From the appearance of the address bar, you can only guess how to restrict the output of results using the construct &tbs=qdr: The letter y after it sets a limit of one year (&tbs=qdr:y), m shows results for the last month, w - for the week, d - for the past day, h - for the last hour, n - for the minute, and s-for the second. The most recent results that have just become known to Google can be found using a filter &tbs=qdr:1.
If you need to write a clever script, it will be useful to know that the date range is set in Google in the Julian format using the operator daterange. For example, this is how you can find a list of PDF documents with the word confidential uploaded from January 1 to July 1, 2015.
Code:
confidential filetypedf daterange:2457024-2457205
The range is specified in the format of Julian dates without taking into account the fractional part. It is inconvenient to translate them manually from the Gregorian calendar. It's easier to use the date Converter.
Targeting and filtering again
In addition to specifying additional operators in the search query, you can send them directly in the link body. For example, filetype dfa construction corresponds to a refinement as_filetype=pdf. This makes it convenient to set any details. Let's say that results are displayed only from the Republic of Honduras by adding the construction to the search URLcr=countryHN, and only from the city of Bobruisk - gcs=Bobruisk. In the developer section, you can find the full list.
dfa construction corresponds to a refinement as_filetype=pdf. This makes it convenient to set any details. Let's say that results are displayed only from the Republic of Honduras by adding the construction to the search URLcr=countryHN, and only from the city of Bobruisk - gcs=Bobruisk. In the developer section, you can find the full list.
Google's automation tools are designed to make life easier, but they often add problems. For example, a user's IP address is used to determine their city via WHOIS. Based on this information, Google not only balances the load between servers, but also changes the search results. Depending on the region, the same request will get different results on the first page, and some of them may be hidden altogether. Feel like a cosmopolitan and search for information from any country will help its two-letter code after the Directive. gl=country. For example, the code of the Netherlands is NL, and the Vatican and North Korea are not allowed to have their own code in Google.
Often, the search results are littered even after using several advanced filters. In this case, it is easy to Refine the query by adding a few exception words (each of them is preceded by a minus sign). For example, the word Personal is often used bankingwith, namesand tutorial. Therefore, cleaner search results will be shown not by a textbook example of a query, but by a refined one:
Code:
intitle:"Index of /Personal/" -names -tutorial -banking
Finally, an example
A sophisticated hacker is distinguished by the fact that he provides himself with everything necessary on his own. For example, a VPN is a convenient thing, but either expensive, or temporary and with restrictions. It's too expensive to subscribe for yourself alone. It's good that there are group subscriptions, and with the help of Google, it's easy to become part of a group. To do this, just find the Cisco VPN configuration file, which has a rather non-standard extension PCFand a recognizable path: Program Files\Cisco Systems\VPN Client\Profiles. One request, and you join, for example, the friendly team of the University of Bonn.
Code:
filetypecf vpn OR Group
Getting into the University of Bonn is significantly more difficult than connecting to their VPN
INFO
Google finds configuration files with passwords, but many of them are written in encrypted form or replaced with hashes. If you see fixed-length strings, then immediately look for a decryption service.
Passwords are stored in encrypted form, but Maurice Massard has already written a program to decrypt them and provides it for free via thecampusgeeks.com.
With the help of Google are hundreds of different types of attacks and penetration testing. There are many options that affect popular programs, major database formats, numerous vulnerabilities in PHP, clouds, and so on. If you know exactly what you're looking for, it will make it much easier to get the information you need (especially if you didn't plan to make it publicly available). Shodan is not the only one that feeds interesting ideas, but every database of indexed network resources!
Looking for files
Filtering the search results
We use bureaucracy
Climbing into the clouds
Spying on configs
Reveal passwords from the database
Don't forget the obvious
Keep an eye out for updates
Targeting and filtering again
Finally, an example
Getting private data does not always mean hacking - sometimes it is published in the public domain. Knowledge of Google settings and a little ingenuity will allow you to find a lot of interesting things-from credit card numbers to FBI documents.
WARNING
All information is provided for informational purposes only. The author are responsible for any possible damage caused by the materials of this article.
Everyone is connected to the Internet today, not caring much about restricting access. Therefore, many private data become the prey of search engines. Spider robots no longer limit themselves to web pages, but index all the content available on the Web and constantly add information that is not intended for disclosure to their databases. It's easy to learn these secrets - you just need to know how to ask about them.
Looking for files
In the right hands, Google will quickly find everything that is bad on the Web - such as personal information and files for official use. They are often hidden like a key under a rug: there are no real access restrictions, the data just lies in the back of the site, where links do not lead. Google's standard web interface provides only basic advanced search settings, but even that will be enough.
You can restrict the search for certain types of files in Google by using two operators: filetypeand ext. The first one sets the format that the search engine determined by the file header, and the second one sets the file extension, regardless of its internal content. When searching in both cases, you only need to specify the extension. Initially, the operator ext it was convenient to use it in cases where there were no specific features of the file format (for example, to search for ini and cfg configuration files, which can contain anything). Now Google's algorithms have changed, and there is no visible difference between the operators — the results in most cases are the same.

Search results with filetype and ext are now the same Search results with filetype and ext are now the same
WWW
Examples of using advanced search operators in Google
Updated selection of Google dorks
Filtering the search results
By default, Google searches all files on indexed pages for words and any characters you enter. You can limit the search area by top-level domain, specific site, or by the location of the search sequence in the files themselves. For the first two options, the site statement is used, followed by the name of the domain or selected site. In the third case, a whole set of operators allows you to search for information in service fields and metadata. For example, allinurlit will find what is specified in the body of the links allinanchorthemselves - in the tagged text<a name>, allintitlein page headers, allintextand in the body of pages.
For each operator, there is a lightweight version with a shorter name (without the prefix all). The difference is that allinurlit will find links with all the words, but inurlonly with the first one. The second and subsequent words from the query can occur anywhere on web pages. The operator inurlalso has differences from another similar meaning - site. The first one also allows you to find any sequence of characters in the link to the desired document (for example, /cgi-bin/), which is widely used to search for components with known vulnerabilities.
Let's try it in practice. We take the filter allintextand make sure that the request returns a list of credit card numbers and verification codes that will expire only in two years (or when their owners get tired of feeding everyone in a row).
Code:
allintext: card number expiration date /2017 cvv

275 thousand actual credit cards, fakes and honeypots for freebie lovers
When you read in the news that a young hacker "hacked the servers" of the Pentagon or NASA, stealing classified information, then in most cases we are talking about this elementary technique of using Google. Suppose we are interested in a list of NASA employees and their contact details. Surely such a list is available in electronic form. For convenience or due to an oversight, it may also be located on the organization's website itself. It is logical that in this case it will not be referenced, since it is intended for internal use. What words can be in such a file? At least - the "address" field. Check out all of these simple assumptions.

Using two operators, you can get "secret" NASA documents in 0.36 seconds
We write
Code:
inurl:nasa.gov filetype:xlsx "address"
and we get links to files with lists of employees.
Addresses and phone numbers of key NASA employees in an Excel file
We use bureaucracy
Such findings are a pleasant trifle. A truly solid catch is provided by a more detailed knowledge of Google operators for webmasters, the Network itself, and the structure of the search engine. Knowing the details, you can easily filter the output and Refine the properties of the necessary files to get really valuable data in the balance. It's funny that bureaucracy comes to the rescue here. It produces standard formulations that make it convenient to search for secret information that has accidentally leaked to the Network.
For example, the Distribution statement stamp required by the office of the United States Department of defense means standardized restrictions on the distribution of a document. The letter A indicates public releases that do not contain anything secret; B - intended only for internal use, C - strictly confidential, and so on up to F. Separately, there is the letter X, which marks particularly valuable information that represents a state secret of the highest level. Let those who are supposed to do it on duty look for such documents, and we will limit ourselves to files with the letter C. According to the DoDI Directive 5230.24, this marking is assigned to documents containing descriptions of critical technologies that fall under export control. You can find such carefully protected information on sites in the .mil top-level domain allocated to the US army.
Code:
"DISTRIBUTION STATEMENT C" inurl:navy.mil

Example of a stamp in a security level C document
It is very convenient that in the domain .mil contains only sites from the US Department of defense and its contract organizations. Search results with domain restrictions are exceptionally clean, and the headlines speak for themselves. It is almost useless to search for Russian secrets in this way: in the domains. ru and .the Russian Federation is in chaos, and the names of many weapons systems sound like Botanical (PP "Cypress", ACS "acacia") or even fabulous (CBT "Pinocchio").

Drawing from the manual for the combat training helicopter TH-57C Sea Ranger
After carefully studying any document from the site in the .mil domain, you can see other markers to Refine the search. For example, a reference to the export restrictions "Sec 2751", which is also convenient to search for interesting technical information. From time to time, it is removed from official sites where it once appeared, so if you can't click on an interesting link in the search results, use The Google cache (cache operator) or the Internet Archive site.
Climbing into the clouds
In addition to accidentally declassified government documents, links to personal files from Dropbox and other data storage services sometimes pop up in Google's cache, which create "private" links to publicly published data. Alternative and self-made services are even worse. For example, the following query finds data from all Verizon customers who have an FTP server installed on their router and are actively using it.
Code:
allinurl:ftp:// verizon.net
There are now more than forty thousand such smart guys, and in the spring of 2015 there were an order of magnitude more of them. InsteadVerizon.net, you can substitute the name of any known provider, and the more famous it is, the bigger the catch may be. The built-in FTP server lets you view files on an external storage device connected to the router. Usually this is a NAS for remote work, a personal cloud, or some kind of peer-to-peer file rocker. All the contents of such media are indexed by Google and other search engines, so you can access files stored on external disks by using a direct link.

Serial numbers, documents, and forty thousand more files from private clouds
Spying on configs
Before the mass migration to the cloud, simple FTP servers were used as remote repositories, which also had enough vulnerabilities. Many of them are still relevant today. For example, the popular WS_FTP Professional program stores configuration data, user accounts, and passwords in a file ws_ftp.ini. It is easy to find and read, since all entries are saved in text format, and passwords are encrypted using the Triple DES algorithm after minimal obfuscation. In most versions, just discard the first byte.

One of the ws_ftp.ini files is publicly available
It is easy to decrypt such passwords using the WS_FTP Password Decryptor utility or a free web service.

Decrypting the password takes about a second
When talking about hacking an arbitrary site, they usually mean getting a password from logs and backups of CMS configuration files or e-Commerce applications. If you know their typical structure, you can easily specify keywords. Strings like those found in ws_ftp.iniare extremely common. For example, Drupal and PrestaShop must have a user ID (UID) and a corresponding password (pwd), and all information is stored in files with the .inc extension. You can search for them in the following way:
Code:
"pwd=" "UID=" ext:inc
Reveal passwords from the database
In the configuration files of SQL servers, users ' names and email addresses are stored in clear text, and their MD5 hashes are written instead of passwords. Strictly speaking, it is impossible to decrypt them, but you can find a match among the known hash-password pairs.

Selecting a password based on the MD5 hash
Until now, there are DBMSs that do not even use password hashing. You can simply view the configuration files of any of them in the browser.
Code:
intextB_PASSWORD filetype:env

The database password is openly stored in the configuration file
With the advent of Windows servers, the registry partially took the place of configuration files. You can search through its branches in the same way, using reg as the file type. For example, like this:
Code:
filetype:reg HKEY_CURRENT_USER "Password"=
The servers with the Windows open

Don't forget the obvious
Sometimes it is possible to get to private information using data that is accidentally opened and caught in the field of view of Google. The ideal option is to find a list of passwords in some common format. Only desperate people can store account information in a text file, Word document, or Excel spreadsheet, but there are always enough of them.
Code:
filetype:xls inurlassword

Li denghui national research Institute of health accidentally revealed a list of passwords
On the one hand, there are a lot of tools to prevent such incidents. You must specify adequate access rights in htaccess, patch the CMS, do not use left-hand scripts, and close other holes. There is also a file with a list of exceptions robots.txt, which prohibits search engines from indexing the files and directories specified in it. On the other hand, if the structure robots.txt if it differs from the standard one on some server, then you can immediately see what they are trying to hide on it.

White house welcomes robots White house welcomes robots
The list of directories and files on any site is preceded by the standard index of label. Since it must appear in the header for official purposes, it makes sense to limit its search to the operator intitle. Interesting things can be found in the /admin/, /personal/, /etc/, and even /secret/directories.

Goolge helps you get to the root of the directory list
Keep an eye out for updates
There are so many leaky systems today that the problem is no longer finding one of them, but choosing the most interesting ones (to study and improve your own security, of course). Examples of search queries that reveal someone's secrets are called Google dorks. One of the first utilities to automatically check the security of sites based on known Google queries was McAfee SiteDigger, but its latest version was released in 2009. Now there are a lot of other tools available to simplify the search for vulnerabilities. For example, SearchDiggity by Bishop Fox, as well as top-UPS databases with a selection of current examples.
Relevance here is extremely important: old vulnerabilities are closed very slowly, but Google and its search results are constantly changing. There is even a difference between the filter "last second" (&tbs=qdr:s at the end of the request url) and "real-time" (&tbs=qdr:1).
The time interval of the last file update date is also specified implicitly by Google. You can use the graphical web interface to select one of the standard periods (hour, day, week, and so on) or set a date range, but this method is not suitable for automation.
From the appearance of the address bar, you can only guess how to restrict the output of results using the construct &tbs=qdr: The letter y after it sets a limit of one year (&tbs=qdr:y), m shows results for the last month, w - for the week, d - for the past day, h - for the last hour, n - for the minute, and s-for the second. The most recent results that have just become known to Google can be found using a filter &tbs=qdr:1.
If you need to write a clever script, it will be useful to know that the date range is set in Google in the Julian format using the operator daterange. For example, this is how you can find a list of PDF documents with the word confidential uploaded from January 1 to July 1, 2015.
Code:
confidential filetypedf daterange:2457024-2457205
The range is specified in the format of Julian dates without taking into account the fractional part. It is inconvenient to translate them manually from the Gregorian calendar. It's easier to use the date Converter.
Targeting and filtering again
In addition to specifying additional operators in the search query, you can send them directly in the link body. For example, filetype
Google's automation tools are designed to make life easier, but they often add problems. For example, a user's IP address is used to determine their city via WHOIS. Based on this information, Google not only balances the load between servers, but also changes the search results. Depending on the region, the same request will get different results on the first page, and some of them may be hidden altogether. Feel like a cosmopolitan and search for information from any country will help its two-letter code after the Directive. gl=country. For example, the code of the Netherlands is NL, and the Vatican and North Korea are not allowed to have their own code in Google.
Often, the search results are littered even after using several advanced filters. In this case, it is easy to Refine the query by adding a few exception words (each of them is preceded by a minus sign). For example, the word Personal is often used bankingwith, namesand tutorial. Therefore, cleaner search results will be shown not by a textbook example of a query, but by a refined one:
Code:
intitle:"Index of /Personal/" -names -tutorial -banking
Finally, an example
A sophisticated hacker is distinguished by the fact that he provides himself with everything necessary on his own. For example, a VPN is a convenient thing, but either expensive, or temporary and with restrictions. It's too expensive to subscribe for yourself alone. It's good that there are group subscriptions, and with the help of Google, it's easy to become part of a group. To do this, just find the Cisco VPN configuration file, which has a rather non-standard extension PCFand a recognizable path: Program Files\Cisco Systems\VPN Client\Profiles. One request, and you join, for example, the friendly team of the University of Bonn.
Code:
filetypecf vpn OR Group
Getting into the University of Bonn is significantly more difficult than connecting to their VPN
INFO
Google finds configuration files with passwords, but many of them are written in encrypted form or replaced with hashes. If you see fixed-length strings, then immediately look for a decryption service.
Passwords are stored in encrypted form, but Maurice Massard has already written a program to decrypt them and provides it for free via thecampusgeeks.com.
With the help of Google are hundreds of different types of attacks and penetration testing. There are many options that affect popular programs, major database formats, numerous vulnerabilities in PHP, clouds, and so on. If you know exactly what you're looking for, it will make it much easier to get the information you need (especially if you didn't plan to make it publicly available). Shodan is not the only one that feeds interesting ideas, but every database of indexed network resources!





















