The developers warned that due to an error Tor Browser could execute JavaScript code on sites where JavaScript launch was deliberately blocked by the user. Although work is already underway to create a fix, there is no patch yet, and no release date has been announced.
The ability to block JavaScript execution is one of the important security aspects of Tor Browser. It is precisely because the browser is focused on maintaining user privacy (in particular, it masks real IP addresses and does everything to preserve the anonymity of a person) it is often used by journalists, political activists and dissidents in countries with repressive blocking and censorship mode.
It is worth saying that previously there were exploits for Tor Browser that used JavaScript to reveal the real IP address of the user. Some of them were used to expose criminals ( 1 , 2 ), while others were used in unknown circumstances ( 1 , 2 ).
Now, the development team has reported that it found an error in the security settings of the Tor Browser Bundle. So, even if the browser is configured to use the highest level of security (Safest), it still allows the execution of JavaScript code in some situations, even when in theory it should block it.
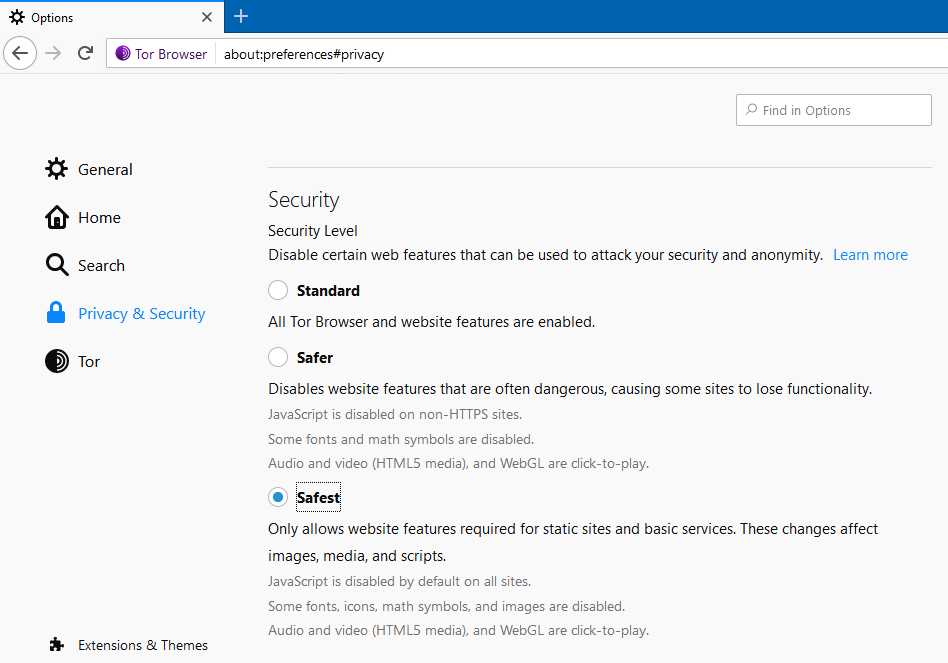
The developers write that they are already working to fix this problem, but while there is no patch, users can completely refuse to use JavaScript and disable it in the settings: about: config -> javascript.enabled -> false.
The ability to block JavaScript execution is one of the important security aspects of Tor Browser. It is precisely because the browser is focused on maintaining user privacy (in particular, it masks real IP addresses and does everything to preserve the anonymity of a person) it is often used by journalists, political activists and dissidents in countries with repressive blocking and censorship mode.
It is worth saying that previously there were exploits for Tor Browser that used JavaScript to reveal the real IP address of the user. Some of them were used to expose criminals ( 1 , 2 ), while others were used in unknown circumstances ( 1 , 2 ).
Now, the development team has reported that it found an error in the security settings of the Tor Browser Bundle. So, even if the browser is configured to use the highest level of security (Safest), it still allows the execution of JavaScript code in some situations, even when in theory it should block it.

The developers write that they are already working to fix this problem, but while there is no patch, users can completely refuse to use JavaScript and disable it in the settings: about: config -> javascript.enabled -> false.



















