New Python Malware Targeting Windows Devices by Carding forum
Named PY#RATION by specialists; the new Python malware is furnished with Rodent conduct and data taking capacities.
The malware includes likewise incorporate document move, keylogging, taking passwords put away in the program, clipboard information taking, treats exfiltration and that's only the tip of the iceberg.
Danger examination firm Securonix's network safety scientists have found a new malware named PY#RATION permitting aggressors to take delicate records and log keystrokes from influenced gadgets.
Malware Dissemination Method
The malware is disseminated through a traditional phishing system in which the email contains a secret phrase safeguarded ZIP chronicle. At the point when it is unloaded, two alternate route picture records show up, named front.jpg.lkn and back.jpg.lnk. At the point when sent off, these documents show the front and back of a driver's permit that doesn't exist.

With this, the vindictive code is additionally executed, prompting two new records being downloaded from the web. These documents are named front.txt and back.txt, later renamed to .bat docs and executed. The malware camouflages itself as Cortana remote helper to guarantee diligence on the framework.
What is PY#RATION
PY#RATION is a Python-based malware that shows a Rodent (remote access trojan) like way of behaving to support command over the impacted host. The malware has different capacities and functionalities, for example, keylogging and information exfiltration.
In any case, the one of a kind viewpoint is that it involves WebSocket for exfiltration and C2 correspondence, and sidesteps identification from network security arrangements and antivirus programs. Utilizing Python's inherent Socket.IO system that works with client and server WebSocket interchanges, the malware pulls information and helps orders over a solitary TCP association through open ports at the same time.

Besides, as per a blog entry distributed by Securonix, the assailants utilize a similar C2 address, which the IPVoid checking framework is yet to obstruct. Scientists accept this malware is still under dynamic advancement as they have identified different renditions since August 2022. The malware gets guidelines from the activities through WebSocket and acquires touchy information.
Expected Risks
This Python Rodent is pressed into an executable that uses robotized packers, for example, 'pyinstaller' and 'py2exe' to change over Python code into Windows executables. This expands payload size (The primary identified rendition 1.0 being 14MB and the last distinguished variant 1.6.0 being 32 MB containing 1000+ lines and extra code).
Specialists guarantee that the most recent variant of the payload stays undetected by all with the exception of one antivirus motor recorded on VirusTotal.
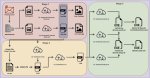
The malware highlights incorporate record move to and from the C2 waiter, network specification, shell order execution, keylogging, taking passwords put away in the program, have count, clipboard information taking, and treats exfiltration. Who's behind this mission, the dispersion volume, and mission goals are as yet muddled.
Named PY#RATION by specialists; the new Python malware is furnished with Rodent conduct and data taking capacities.
The malware includes likewise incorporate document move, keylogging, taking passwords put away in the program, clipboard information taking, treats exfiltration and that's only the tip of the iceberg.
Danger examination firm Securonix's network safety scientists have found a new malware named PY#RATION permitting aggressors to take delicate records and log keystrokes from influenced gadgets.
Malware Dissemination Method
The malware is disseminated through a traditional phishing system in which the email contains a secret phrase safeguarded ZIP chronicle. At the point when it is unloaded, two alternate route picture records show up, named front.jpg.lkn and back.jpg.lnk. At the point when sent off, these documents show the front and back of a driver's permit that doesn't exist.

With this, the vindictive code is additionally executed, prompting two new records being downloaded from the web. These documents are named front.txt and back.txt, later renamed to .bat docs and executed. The malware camouflages itself as Cortana remote helper to guarantee diligence on the framework.
What is PY#RATION
PY#RATION is a Python-based malware that shows a Rodent (remote access trojan) like way of behaving to support command over the impacted host. The malware has different capacities and functionalities, for example, keylogging and information exfiltration.
In any case, the one of a kind viewpoint is that it involves WebSocket for exfiltration and C2 correspondence, and sidesteps identification from network security arrangements and antivirus programs. Utilizing Python's inherent Socket.IO system that works with client and server WebSocket interchanges, the malware pulls information and helps orders over a solitary TCP association through open ports at the same time.

Besides, as per a blog entry distributed by Securonix, the assailants utilize a similar C2 address, which the IPVoid checking framework is yet to obstruct. Scientists accept this malware is still under dynamic advancement as they have identified different renditions since August 2022. The malware gets guidelines from the activities through WebSocket and acquires touchy information.
Expected Risks
This Python Rodent is pressed into an executable that uses robotized packers, for example, 'pyinstaller' and 'py2exe' to change over Python code into Windows executables. This expands payload size (The primary identified rendition 1.0 being 14MB and the last distinguished variant 1.6.0 being 32 MB containing 1000+ lines and extra code).
Specialists guarantee that the most recent variant of the payload stays undetected by all with the exception of one antivirus motor recorded on VirusTotal.

The malware highlights incorporate record move to and from the C2 waiter, network specification, shell order execution, keylogging, taking passwords put away in the program, have count, clipboard information taking, and treats exfiltration. Who's behind this mission, the dispersion volume, and mission goals are as yet muddled.






















