adrik123adi
Well-known member
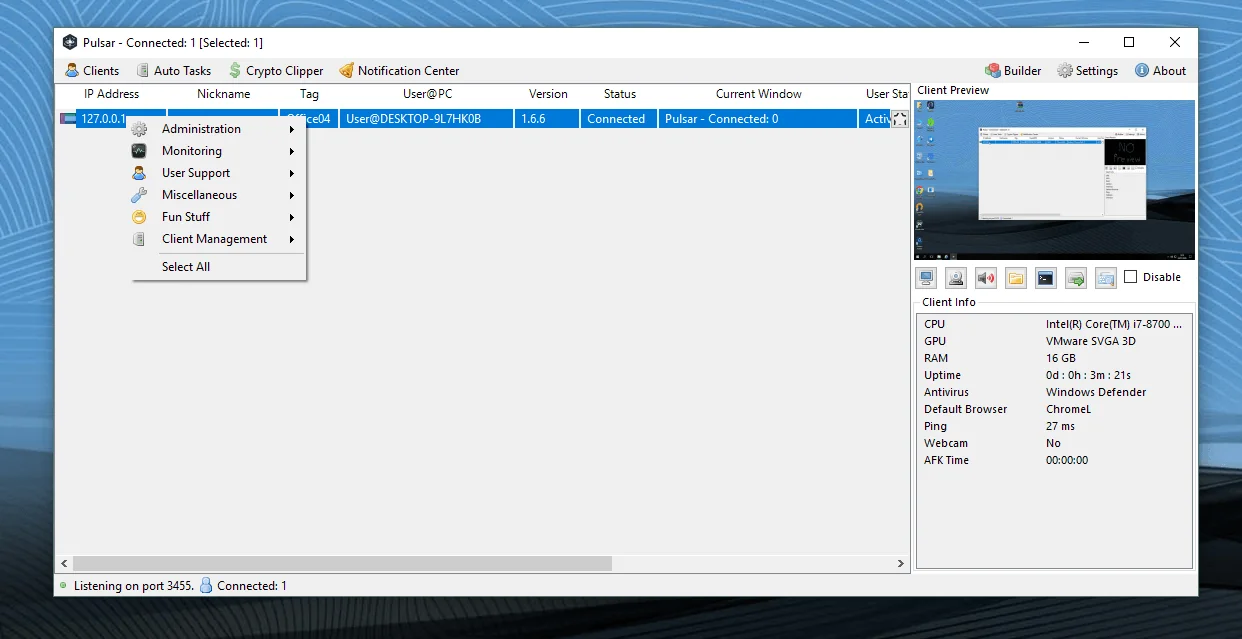
Pulsar RAT 2026
Key Capabilities Discussed in Pulsar RAT 2026 (Cybersecurity Analysis)
Security researchers analyzing Pulsar RAT 2026–style threats often highlight a range of capabilities that explain why modern Remote Access Trojans (RATs) remain a serious concern for individuals and organizations across the US and UK. Understanding these features helps defenders recognize risks and improve prevention strategies.

Improved Connectivity and Stability
Modern RAT variants emphasize faster and more stable remote connections. This allows attackers to maintain persistent access with fewer interruptions, making detection more difficult for traditional security tools.
Enhanced Remote Desktop Performance
Advanced remote desktop functionality may include smoother screen rendering and higher frame rates, sometimes leveraging GPU acceleration technologies. From a defensive standpoint, this means compromised systems can be controlled in near real time, increasing potential damage.
Instant Client Preview
Some RAT threats provide a preview of a compromised system’s desktop along with basic system information. This enables attackers to quickly assess the value of a target, which is why endpoint monitoring and access controls are critical.
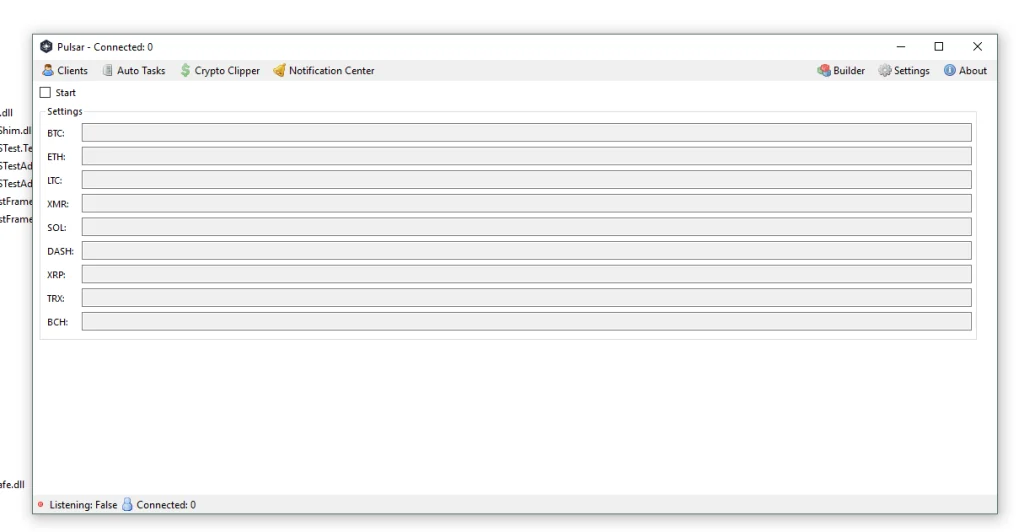
Cryptocurrency Address Manipulation
Crypto address replacement techniques are designed to intercept copied wallet addresses and swap them with attacker-controlled ones. This threat has become increasingly relevant in regions with high crypto adoption, including the US and UK.
Virtual or Invisible Display Environments
Virtual monitor functionality allows attackers to operate within an unseen desktop environment. Because the victim may not notice visible screen activity, such attacks can persist longer without detection.
Memory Extraction Techniques
Memory dumping capabilities enable attackers to extract sensitive data from active processes, potentially bypassing encryption or security protections. This is a major concern for enterprises handling credentials or proprietary data.
Disruptive or Psychological Tactics
Some threats include disruptive actions such as interface manipulation or forced system crashes. While sometimes described as “pranks,” these behaviors can cause data loss, downtime, and user distress.
https://www.virustotal.com/gui/file/f5945fd353dae4f3a4cccdc7159f67f5fd8ff82963f370a80c768efd325694b3

Pulsar Rat 2026
MediaFire is a simple to use free service that lets you put all your photos, documents, music, and video in a single place so you can access them anywhere and share them everywhere.
www.mediafire.com



















