Quite deservedly for a long time, remote access solutions have caused well-deserved distrust among users. Some people and companies refused to use them on principle. The fears are justified: the number of attacks via the remote access protocol is not only growing - during the pandemic, it generally doubled.
We will tell you about what an RDP attack is, how to detect it and how to defend against it on an ongoing basis, and which methods are not so effective.
Until recently, corporate data traffic in the vast majority of cases circulated in a controlled infrastructure. But the pandemic has forced people to rush to roll out access to corporate environments at home and unsecured Wi-Fi networks. Well, the love of users for simple passwords and dislike for two-factor authentication have always been a headache for admins.
Cybercriminals immediately took advantage of this. Since the beginning of strict quarantine, the already “popular” attacks via remote access protocols have increased exponentially: almost a million such attempts have been registered every day. The most popular of the remote access protocols is Microsoft's proprietary RDP protocol, which is why these attacks are called RDP attacks. Although, to one degree or another, any remote access solution is vulnerable.
Statistics
According to Kaspersky Lab, since the beginning of March 2020, the number of attacks on RDP has increased in leaps and bounds. ESET in its report said on more than 100 thousand new RDP-attacks per day - an increase of more than doubled compared with the first quarter.
The reason, among other things, is not only in the transition to remote work, but also in a hurry - for companies when moving to quarantine, the main thing was to ensure the operability of the infrastructure, and its safety was only the second task. For example, a survey of information security specialists conducted at Positive Technologies showed that due to the pandemic, they had to either urgently organize remote access from scratch (11%) or urgently scale up (41%).
What are RDP attacks
RDP (Remote Desktop Protocol) is one of the most popular protocols for connecting to remote desktops, available in all versions of Windows starting from XP. In addition to interacting with a remote computer, it allows you to connect local disks, ports, and other devices to a remote machine. It is used by most administrators of Windows environments to administer user workstations and servers, saving them a lot of time.
Vulnerabilities were constantly found in the protocol, and so often that in 2018 even the FBI issued a special warning. In May 2019, a critical vulnerability called BlueKeep was discovered in older versions of the protocol. Just a month after its appearance, an active wave of attacks using BlueKeep began. Then, in August of that year, four more new vulnerabilities were found in the protocol. They were not related to the RDP protocol, but to the RDS remote desktop service and allowed, using a special request sent via RDP, to access the vulnerable system without going through the authentication procedure.
An RDP attack is, in fact, a brute force attack, during which a username and password or an encryption key for accessing RDP is brute-force by systematically enumerating all possible combinations of characters until the correct one is found. For long passwords, dictionary brute force can be used, where instead of generating a combination of letters and numbers, a long list of popular or compromised passwords is used.
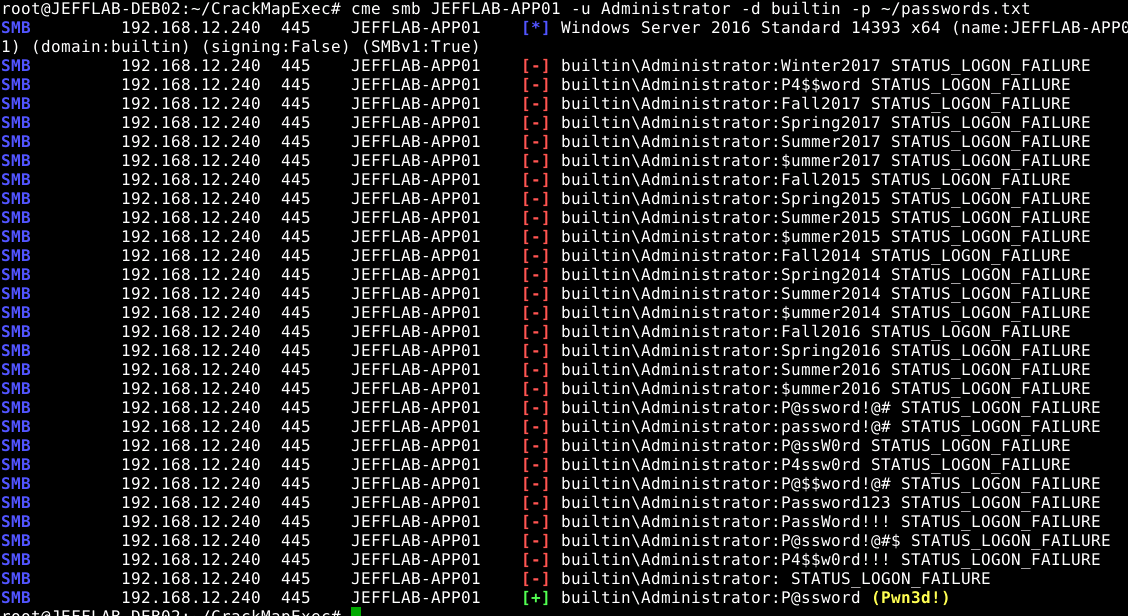
The goal is to gain full remote access to the desired computer or server and penetrate through it into the corporate network, having all the appropriate rights and access. The attacker infiltrates the dialogue between two systems at the moment of establishing an RDP session and, having decrypted the packet, gains full access to the remote system, and without any notifications on the client or server side, since he has a “correct” certificate.
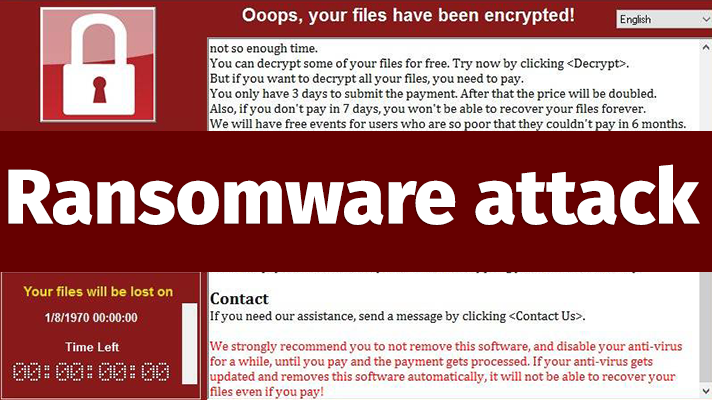
And then the attack itself begins from within the system. Security solutions are disabled or removed, and then either a DDoS attack begins, or a ransomware program is launched that sets a password to access databases of information that is important to the company. Or, real personal data is taken away for credential stuffing and phishing. You can also use a poorly protected RDP to install programs for mining cryptocurrencies or create a backdoor (in case unauthorized access to RDP is detected and blocked), to install adware or spyware, SMS Trojans, and so on. This can completely infect all machines available on the network.
There are scripts that are able to maximize the rights of the user who connects via RDP and all subsequent users in the chain of RDP connections. This method is called RDPInception. If the attacked machine is connected in a chain through several servers and local disks are mounted everywhere, then the script is self-copied to the necessary directories and it becomes possible to attack all machines, since the scripts located in the Startup directory are executed when entering the system. Anything connected in this chain can also be infected.
Why are they dangerous?
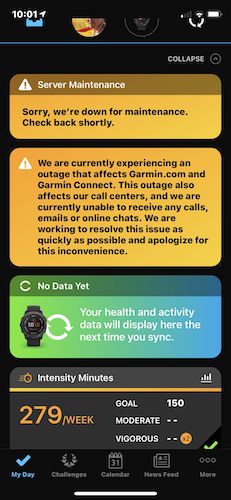
A poorly secured RDP connection can provide criminals with access to the entire corporate system. For example, encrypting a company's servers with ransomware and then demanding a ransom can be extremely damaging to a business. This is indicative of the recent story of a very large GPS vendor Garmin, which was forced to pay the extortionists $ 10 million - otherwise their security specialists failed to solve the problem.
Technically, such attacks are also becoming more and more dangerous. First, attackers no longer work point-to-point, but cover large segments of networks.
Second, the time for simple attacks has passed. Criminals use complex schemes and a combination of methods. For example, the TrickBot Trojan has a new rdpScanDll module, which is used to carry out brute force attacks on RDP connections. This module has already been featured in a number of attacks on large companies, including those related to education and finance.
Third, personal data and hacking tools are unfortunately becoming more and more accessible. For example, recently the source code of Dharma, a ransomware-as-a-service software that also targets RDP, was released for sale online (sorry, we will not provide a link). The number of leaks of databases with passwords and dictionaries for brute-forcing passwords is growing, the above-mentioned cracking scripts can be found in the public domain, and there are ready-made lists of servers that have an open RDP port. There are a huge number of bots on the market that constantly scan all available connection points and try to guess the password.
Finally, the means of protection are either insufficient for “brute-forcing passwords”, or they are not applied. Companies often don't even see that such an attack is underway. They may notice poor performance and long query execution times, but treat this with memory optimizations and other irrelevant methods.
How to understand that an RDP attack has started
Ways to get rid of them
There are, in fact, many ways, but in this article we decided to divide them into completely reliable ones and those that either have certain drawbacks, or they are difficult to implement, or they can only serve as a temporary measure. Let's start with the reliable ones.
Correct password system
A recent study by Verizon showed that more than 80% of hacks are not related to vulnerabilities in the RDP protocol, but rather to weak passwords. Therefore, companies must adopt and consolidate in the infrastructure a policy of using difficult-to-guess passwords and mandatory two-factor authentication. It is desirable to store passwords for users in special protected password managers. Security solutions should also be additionally password protected so that they cannot be disabled from the inside if an attack is successful.
Monitoring system for all requests
An effective way is to monitor all incoming traffic and track all unauthorized connections and requests. Some additional tracking systems can be added to the monitoring systems for remote connections, which will help to see a more complete picture of what is happening.
Another option: if there is no centralized access control system, then you can create a powershell script that reports all facts and authorization attempts. Finally, you can configure “Events” to display all available information.
Network Level Authentication
NLA provides stronger protection against key spoofing by requiring authentication before establishing a session and during a session. Last year, it was the NLA that made it difficult to exploit serious vulnerabilities in the protocol.
A number of other useful practices:
Organize VPN access
Besides the obvious advantages, this option has several complications.
Use other means of remote access
Unfortunately, they also have vulnerabilities. For example, at the end of last year, 37 vulnerabilities were found in different clients working with the VNC protocol.
Change the settings of all users to a different port
Probably the least reliable method of all, although there are sure to be people out there who work great for this. Why is he “not very”?
Introduce various restrictions on connections
For example, you can limit the number of allowed simultaneously open sessions, minimize the number of users who can connect to the company's servers via the Internet, deny access to the server from more than N IP addresses, limit the number of allowed erroneous login attempts and the time for these attempts, set the blocking time for login in case of incorrect password entry, and so on. Yes, it helps, but it is not a complete solution. Unfortunately, as practice shows, these measures may not give a noticeable decrease in the number of attacks, because bots work around the clock and without stopping, and restrictions are a bunch of fine settings, where one depends on the other, and the administrator himself often has certain restrictions on the settings.
IP blocking
An effective method for the generation of "kulkhatskers" - blocking IP - in the case of serious opponents can be useless, if not dangerous. In any case, the addresses from which attacks originate vary in a very wide range (brute-force attacks often come from a group of addresses and even from different subnets), so the very idea of blocking by addresses is a treatment of consequences, not a disease. An IP address is too easy to spoof, attackers can use hundreds and easily change them. And there is a high probability that they will substitute it in such a way that your own address or the IP of your clients will be blocked.
Also, blocking individual IPs on a Windows server is not an easy task. Firstly, the IP of the one who is trying to connect is often not visible in the security logs - in some cases it can be seen only after successful authorization. Otherwise, only the login under which they tried to log in is visible, although the events are noted in the log. And it is even more difficult if the IP is specially hidden.
By the way, if you do this using the Windows Firewall, then after a while Windows starts to slow down a lot due to the overflowing Windows Firewall rule.
Giving access to data only to a whitelist of IP addresses is also a rather difficult thing in a remote location and home offices - IP can float, since the user uses very different gadgets that are “on the farm”, and everyone strives to work from a cafe or park with public Wi-Fi.
Brave new world
For many companies, telecommuting is likely to remain a permanent part of their culture, and something needs to be done about it. At the same time, vulnerabilities in RDP surface constantly, and you have to regularly google what has appeared new.
The main headache in protecting yourself from RDP attacks in such a situation is the zoo of devices on which employees work remotely, and the time frame, since the problem needs to be solved quickly. And there is no need to explain that in each specific organization the administrator may have separate restrictions - someone is allocated only one port for the service, someone does not have the right hardware and a sufficient budget.
There is probably no single answer to how to completely protect yourself from such attacks using a single tool (but we think the market is working hard on this). In addition, bots have become much more cunning and more complex, and hackers have become smarter, and attacks have become more multifaceted. A set of measures will be required, because there are still quite a lot of protection options, in addition to those that we have written about, including hardware - firewalls, routers, virtualization, separation of the main database and much more.
But, we are sure that the most important and first step is to clearly see if you have such a problem and how serious it is. So turn on your monitors. The second step is to do whatever it takes to make the hacker's life as difficult as possible. There is a huge chance that, faced with at least a few tricks, the hacker will not waste time on you, but will find an easier victim.
We will tell you about what an RDP attack is, how to detect it and how to defend against it on an ongoing basis, and which methods are not so effective.
Until recently, corporate data traffic in the vast majority of cases circulated in a controlled infrastructure. But the pandemic has forced people to rush to roll out access to corporate environments at home and unsecured Wi-Fi networks. Well, the love of users for simple passwords and dislike for two-factor authentication have always been a headache for admins.
Cybercriminals immediately took advantage of this. Since the beginning of strict quarantine, the already “popular” attacks via remote access protocols have increased exponentially: almost a million such attempts have been registered every day. The most popular of the remote access protocols is Microsoft's proprietary RDP protocol, which is why these attacks are called RDP attacks. Although, to one degree or another, any remote access solution is vulnerable.
Statistics
According to Kaspersky Lab, since the beginning of March 2020, the number of attacks on RDP has increased in leaps and bounds. ESET in its report said on more than 100 thousand new RDP-attacks per day - an increase of more than doubled compared with the first quarter.
The reason, among other things, is not only in the transition to remote work, but also in a hurry - for companies when moving to quarantine, the main thing was to ensure the operability of the infrastructure, and its safety was only the second task. For example, a survey of information security specialists conducted at Positive Technologies showed that due to the pandemic, they had to either urgently organize remote access from scratch (11%) or urgently scale up (41%).
What are RDP attacks
RDP (Remote Desktop Protocol) is one of the most popular protocols for connecting to remote desktops, available in all versions of Windows starting from XP. In addition to interacting with a remote computer, it allows you to connect local disks, ports, and other devices to a remote machine. It is used by most administrators of Windows environments to administer user workstations and servers, saving them a lot of time.
Vulnerabilities were constantly found in the protocol, and so often that in 2018 even the FBI issued a special warning. In May 2019, a critical vulnerability called BlueKeep was discovered in older versions of the protocol. Just a month after its appearance, an active wave of attacks using BlueKeep began. Then, in August of that year, four more new vulnerabilities were found in the protocol. They were not related to the RDP protocol, but to the RDS remote desktop service and allowed, using a special request sent via RDP, to access the vulnerable system without going through the authentication procedure.
An RDP attack is, in fact, a brute force attack, during which a username and password or an encryption key for accessing RDP is brute-force by systematically enumerating all possible combinations of characters until the correct one is found. For long passwords, dictionary brute force can be used, where instead of generating a combination of letters and numbers, a long list of popular or compromised passwords is used.
The goal is to gain full remote access to the desired computer or server and penetrate through it into the corporate network, having all the appropriate rights and access. The attacker infiltrates the dialogue between two systems at the moment of establishing an RDP session and, having decrypted the packet, gains full access to the remote system, and without any notifications on the client or server side, since he has a “correct” certificate.
And then the attack itself begins from within the system. Security solutions are disabled or removed, and then either a DDoS attack begins, or a ransomware program is launched that sets a password to access databases of information that is important to the company. Or, real personal data is taken away for credential stuffing and phishing. You can also use a poorly protected RDP to install programs for mining cryptocurrencies or create a backdoor (in case unauthorized access to RDP is detected and blocked), to install adware or spyware, SMS Trojans, and so on. This can completely infect all machines available on the network.
There are scripts that are able to maximize the rights of the user who connects via RDP and all subsequent users in the chain of RDP connections. This method is called RDPInception. If the attacked machine is connected in a chain through several servers and local disks are mounted everywhere, then the script is self-copied to the necessary directories and it becomes possible to attack all machines, since the scripts located in the Startup directory are executed when entering the system. Anything connected in this chain can also be infected.
Why are they dangerous?
A poorly secured RDP connection can provide criminals with access to the entire corporate system. For example, encrypting a company's servers with ransomware and then demanding a ransom can be extremely damaging to a business. This is indicative of the recent story of a very large GPS vendor Garmin, which was forced to pay the extortionists $ 10 million - otherwise their security specialists failed to solve the problem.

Technically, such attacks are also becoming more and more dangerous. First, attackers no longer work point-to-point, but cover large segments of networks.
Second, the time for simple attacks has passed. Criminals use complex schemes and a combination of methods. For example, the TrickBot Trojan has a new rdpScanDll module, which is used to carry out brute force attacks on RDP connections. This module has already been featured in a number of attacks on large companies, including those related to education and finance.
Third, personal data and hacking tools are unfortunately becoming more and more accessible. For example, recently the source code of Dharma, a ransomware-as-a-service software that also targets RDP, was released for sale online (sorry, we will not provide a link). The number of leaks of databases with passwords and dictionaries for brute-forcing passwords is growing, the above-mentioned cracking scripts can be found in the public domain, and there are ready-made lists of servers that have an open RDP port. There are a huge number of bots on the market that constantly scan all available connection points and try to guess the password.
Finally, the means of protection are either insufficient for “brute-forcing passwords”, or they are not applied. Companies often don't even see that such an attack is underway. They may notice poor performance and long query execution times, but treat this with memory optimizations and other irrelevant methods.
How to understand that an RDP attack has started
- The overall performance decreases, the responses to requests take longer (and sometimes you don't see this in the traffic - there are no obvious spikes or dips, and there are no anomalies in the statistics of the load on computational resources).
- The servers do not accept connections to the remote access service, and users cannot access their desktops. In this case, the situation can temporarily improve, then worsen. In general, servers can be accessed and even pinged.
- In the event logs, you see a lot of messages about trying to guess the password (unfortunately, not always - there are often no attempts to enter the wrong username and password, because tracking these events puts a heavy load on the server).
Ways to get rid of them
There are, in fact, many ways, but in this article we decided to divide them into completely reliable ones and those that either have certain drawbacks, or they are difficult to implement, or they can only serve as a temporary measure. Let's start with the reliable ones.
Correct password system
A recent study by Verizon showed that more than 80% of hacks are not related to vulnerabilities in the RDP protocol, but rather to weak passwords. Therefore, companies must adopt and consolidate in the infrastructure a policy of using difficult-to-guess passwords and mandatory two-factor authentication. It is desirable to store passwords for users in special protected password managers. Security solutions should also be additionally password protected so that they cannot be disabled from the inside if an attack is successful.
Monitoring system for all requests
An effective way is to monitor all incoming traffic and track all unauthorized connections and requests. Some additional tracking systems can be added to the monitoring systems for remote connections, which will help to see a more complete picture of what is happening.
Another option: if there is no centralized access control system, then you can create a powershell script that reports all facts and authorization attempts. Finally, you can configure “Events” to display all available information.
Network Level Authentication
NLA provides stronger protection against key spoofing by requiring authentication before establishing a session and during a session. Last year, it was the NLA that made it difficult to exploit serious vulnerabilities in the protocol.
A number of other useful practices:
- Use non-standard keys such as PKI (Public Key Infrastructure), and use TLS (Transport Layer Security) for RDP connections.
- If RDP is not used, then disable it and disable external connections to local machines on port 3389 (TCP / UDP) or any other RDP port on the network firewall.
- Constantly update all software on employees' devices to the latest versions. Remember that 80-90% of exploits were created after a vulnerability patch was released. Having learned that there was a vulnerability, the attackers are looking for it in older versions of the software. Of course, this is not an easy task in a remote environment, but it should be part of corporate IT policy. In addition, any unsecured or outdated computers should be isolated.
- Whenever possible, use encryption on devices that are used for work tasks (such as disk encryption).
- Back up key data. Backups should only be available to the administrator or backup user. Folder rights to backup files should also be limited as much as possible.
- Install security solutions and solutions on all employee devices to track equipment in case of loss.
Organize VPN access
Besides the obvious advantages, this option has several complications.
- Even those using the Virtual Private Network are sometimes allowed to authenticate the user without a password.
- Almost all popular VPN solutions also have unauthorized access vulnerabilities.
- If you haven’t used a VPN before, setting up IPSec connections in a hurry is not an easy task.
- In the conditions of a complete home “zoo” of devices and network connections (how about accessing the Internet via a cellular modem?) It is rather difficult to explain and configure each of several hundred users at a remote location so that the user will work stably and the network connection will not be lost.
- VPN servers can also crash, and unlike a temporary drop in any of the services, this can threaten with serious consequences. It turns out that VPN servers are becoming a single point of failure with all the ensuing consequences.
- VPN is double encryption (in addition to standard RDP encryption, VPN encryption is additionally performed), which means an additional load and a slower connection, which is not very good in an unstable or not particularly fast communication channel.
- When a VPN is hacked (and this can be when a router is hacked), if it is configured by default (or not competently enough), the hacker immediately gains access to the entire internal network, in contrast to access to a single PC in the event of an RDP hack (although through it too then you can access the internal network).
Use other means of remote access
Unfortunately, they also have vulnerabilities. For example, at the end of last year, 37 vulnerabilities were found in different clients working with the VNC protocol.
Change the settings of all users to a different port
Probably the least reliable method of all, although there are sure to be people out there who work great for this. Why is he “not very”?
- It takes a long time to change the settings if you have many end users, which may include clients. But the count often goes by minutes during the active phase of the attacks. In this situation, you need to fix the problem as soon as possible with minimal disruption of users from business.
- It is also a temporary solution because modern bots with intelligent port scanning software will quickly find a new non-standard port. From our anti-bot practice: bots catch a non-standard port from a couple of hours to a couple of days. In general, they will still come to you, albeit later. Perhaps renaming accounts of the type Administrator, admin, user, user1 to more non-dictionary ones will be even more efficient here.
Introduce various restrictions on connections
For example, you can limit the number of allowed simultaneously open sessions, minimize the number of users who can connect to the company's servers via the Internet, deny access to the server from more than N IP addresses, limit the number of allowed erroneous login attempts and the time for these attempts, set the blocking time for login in case of incorrect password entry, and so on. Yes, it helps, but it is not a complete solution. Unfortunately, as practice shows, these measures may not give a noticeable decrease in the number of attacks, because bots work around the clock and without stopping, and restrictions are a bunch of fine settings, where one depends on the other, and the administrator himself often has certain restrictions on the settings.
IP blocking
An effective method for the generation of "kulkhatskers" - blocking IP - in the case of serious opponents can be useless, if not dangerous. In any case, the addresses from which attacks originate vary in a very wide range (brute-force attacks often come from a group of addresses and even from different subnets), so the very idea of blocking by addresses is a treatment of consequences, not a disease. An IP address is too easy to spoof, attackers can use hundreds and easily change them. And there is a high probability that they will substitute it in such a way that your own address or the IP of your clients will be blocked.
Also, blocking individual IPs on a Windows server is not an easy task. Firstly, the IP of the one who is trying to connect is often not visible in the security logs - in some cases it can be seen only after successful authorization. Otherwise, only the login under which they tried to log in is visible, although the events are noted in the log. And it is even more difficult if the IP is specially hidden.
By the way, if you do this using the Windows Firewall, then after a while Windows starts to slow down a lot due to the overflowing Windows Firewall rule.
Giving access to data only to a whitelist of IP addresses is also a rather difficult thing in a remote location and home offices - IP can float, since the user uses very different gadgets that are “on the farm”, and everyone strives to work from a cafe or park with public Wi-Fi.
Brave new world
For many companies, telecommuting is likely to remain a permanent part of their culture, and something needs to be done about it. At the same time, vulnerabilities in RDP surface constantly, and you have to regularly google what has appeared new.
The main headache in protecting yourself from RDP attacks in such a situation is the zoo of devices on which employees work remotely, and the time frame, since the problem needs to be solved quickly. And there is no need to explain that in each specific organization the administrator may have separate restrictions - someone is allocated only one port for the service, someone does not have the right hardware and a sufficient budget.
There is probably no single answer to how to completely protect yourself from such attacks using a single tool (but we think the market is working hard on this). In addition, bots have become much more cunning and more complex, and hackers have become smarter, and attacks have become more multifaceted. A set of measures will be required, because there are still quite a lot of protection options, in addition to those that we have written about, including hardware - firewalls, routers, virtualization, separation of the main database and much more.
But, we are sure that the most important and first step is to clearly see if you have such a problem and how serious it is. So turn on your monitors. The second step is to do whatever it takes to make the hacker's life as difficult as possible. There is a huge chance that, faced with at least a few tricks, the hacker will not waste time on you, but will find an easier victim.



















