o365-attack-toolkit allows operators to perform an OAuth phishing attack and later on use the Microsoft Graph API to extract interesting information.
Some of the implemented features are :
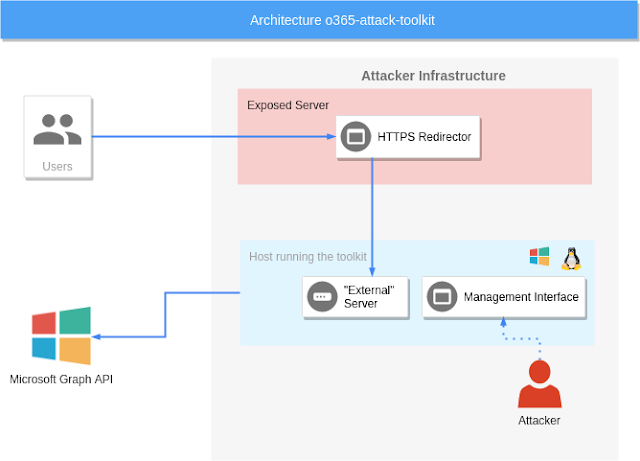
The toolkit consists of several components
Phishing endpoint
The phishing endpoint is responsible for serving the HTML file that performs the OAuth token phishing.
Backend services
Afterward, the token will be used by the backend services to perform the defined attacks.
Management interface
The management interface can be utilized to inspect the extracted information from the Microsoft Graph API.
Some of the implemented features are :
- Extraction of keyworded e-mails from Outlook.
- Creation of Outlook Rules.
- Extraction of files from OneDrive/Sharepoint.
- Injection of macros on Word documents.

The toolkit consists of several components
Phishing endpoint
The phishing endpoint is responsible for serving the HTML file that performs the OAuth token phishing.
Backend services
Afterward, the token will be used by the backend services to perform the defined attacks.
Management interface
The management interface can be utilized to inspect the extracted information from the Microsoft Graph API.

















