EMV, named after its founders Europay, Mastercard and Visa, is the international protocol standard for in-store smart card payments. In December 2020, EMVCo announced that there are 9.89 billion EMV cards in circulation worldwide. Despite the declared security of the standard, various logical flaws have been identified previously, which are difficult to spot in the long and complex EMV specification, spanning over 2,000 pages.
We have defined a comprehensive model (expanded here ) of the EMV protocol using the Tamarin Model Validator... Using our models, we identified several authentication flaws that led to two critical attacks, one affecting Visa and the other affecting Mastercard.
The Visa attack allows attackers to make over-the-limit purchases without a PIN using the victim's contactless Visa card without knowing the card's PIN. In other words, the PIN on your Visa card is useless because it will not protect your card from being used for high-value fraudulent purchases.
The attack on Mastercard allows cybercriminals to trick the terminal into making transactions with the victim's contactless Mastercard, believing it to be a Visa card. Such a mixture of card brandshas critical implications as it can be used in conjunction with Visa PIN Bypass to bypass Mastercard PIN as well. As a result of our disclosure process, Mastercard implemented security mechanisms that we have experimentally proven to be effective against an attack.
[B Demonstration of Attacks [/ B]
To demonstrate the possibility of attacks, we have developed an experimental Android application. Our application implements attacks as “malefactor-in-the-middle” attacks based on the relay attack architecture using two NFC-enabled phones.
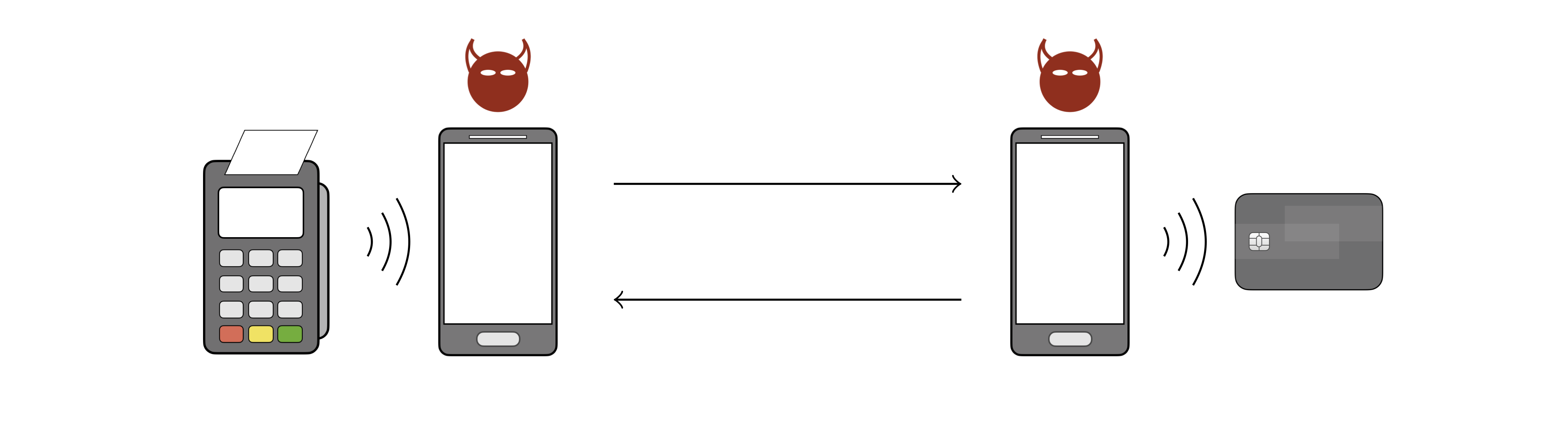
External devices are the payment terminal (left) and the victim's contactless card (right). The phone next to the payment terminal is the attacker's card emulator device, and the phone next to the victim's card is the attacker's POS terminal emulator device. The attacker's devices communicate with each other via Wi-Fi, and with the terminal and card via NFC.
For the attacks to work, the criminals must have access to the victim's card, either by stealing it, finding it if lost, or holding a POS emulator next to it if the victim is still in possession of it. Attacks work by modifying terminal commands and card responses before delivering them to the appropriate recipient.
Our app does not require root privileges or any Android hacks. We used it on Google Pixel 2 XL and Huawei P Smart 2019 devices.
Attack on Visa The
attack consists in modifying the qualifiers of card transactions (CTQ, card data object) before they are delivered to the terminal. The modification tells the terminal that:
This attack can also affect Discover and UnionPay cards. Our findings were published by ETH Zurich , ACM TechNews , Schweizer Radio und Fernsehen (SRF) , The Hacker News , ZDNet , heise , and the full technical report is presented in our article:
EMV Standard: Hack, Fix, Verify
David Basin, Ralph Sasse and Jorge Toro-Pozo 42nd IEEE Security and Privacy Symposium (S&P) 2021
Mastercard Attack
This attack primarily involves replacing the legitimate application identifiers (AIDs) of the card with the Visa AID, A0000000031010, to force the terminal to activate the Visa core. The attacker then simultaneously performs a Visa transaction with a terminal and a Mastercard transaction with a card. In a Visa transaction, the attacker uses the aforementioned attack on Visa.
For this attack to work, the terminal authorization request must go to the issuing bank. Requirements for this include:
This attack can also affect JCB and American Express cards. Our research was published by ETH Zurich , ACM TechNews , The Hacker News , and a full technical report is provided in our article:
Card Brand Mixing Attack: Bypassing PIN in Non-Visa Cards by Using It for Visa Transactions
David Basin. Ralph Sasse and Jorge Toro-Pozo 30th USENIX Security Symposium 2021
Frequently Asked Questions
What cards are affected by these attacks?
We have successfully bypassed the PIN for Visa Credit, Visa Debit, Visa Electron, V Pay, Mastercard Credit and Maestro. Other EMV cards may be affected, but we have no real-world proof of this.
Have there been any reactions from the affected companies?
We have uncovered attacks on both Visa and Mastercard. As a result of our successful Mastercard disclosure process, the payment network has since implemented and deployed defense mechanisms against an attack affecting their cards.
What role did Tamarin play in this study?
Tamarin is a modern verification tool. With its help, we analyzed the full flow of EMV transaction execution with an unlimited number of executions executed simultaneously in a competitive environment, where all messages exchanged between the terminal and the card can be read / blocked / entered. The result of this analysis was the identification of new attacks that we are talking about, as well as the re-detection of existing ones. We also used Tamarin to design and test (under all the adversarial conditions described above) against all attacks.
There used to be many attacks on EMV, how are they different?
The previously reported practical attacks are either conspicuous and therefore difficult to use in practice, or they do not appear to be profitable to criminals due to the fact that they are only possible for inexpensive purchases. Our attacks allow attackers to execute high-value fraudulent transactions using an app that looks just like a commercial payment app such as Apple Pay or Google Pay to avoid detection.
Something went wrong? How can you avoid similar problems in the future?
Important data sent by the card during a transaction is not authenticated. Complex systems such as EMV must be analyzed by automated tools such as model validators. Humans cannot handle the volume of execution and branching phases that a complex system has, so security breaches are often overlooked.
Should our cards be protected in a “metal wallet” to prevent them from being read off remotely?
This can help. Although you still have problems if lost or stolen.
What actions should I take as a citizen now to protect myself?
Bank-recommended protection measures are applied. Block the card immediately after you realize that it is lost or stolen. Check your bank statement regularly and report back to your bank immediately when you see an unrecognized transaction. Also, whenever you carry a contactless EMV card, make sure no one is holding the device next to it against your will. Also be mindful of your back pocket
We have defined a comprehensive model (expanded here ) of the EMV protocol using the Tamarin Model Validator... Using our models, we identified several authentication flaws that led to two critical attacks, one affecting Visa and the other affecting Mastercard.
The Visa attack allows attackers to make over-the-limit purchases without a PIN using the victim's contactless Visa card without knowing the card's PIN. In other words, the PIN on your Visa card is useless because it will not protect your card from being used for high-value fraudulent purchases.
The attack on Mastercard allows cybercriminals to trick the terminal into making transactions with the victim's contactless Mastercard, believing it to be a Visa card. Such a mixture of card brandshas critical implications as it can be used in conjunction with Visa PIN Bypass to bypass Mastercard PIN as well. As a result of our disclosure process, Mastercard implemented security mechanisms that we have experimentally proven to be effective against an attack.
[B Demonstration of Attacks [/ B]
To demonstrate the possibility of attacks, we have developed an experimental Android application. Our application implements attacks as “malefactor-in-the-middle” attacks based on the relay attack architecture using two NFC-enabled phones.

External devices are the payment terminal (left) and the victim's contactless card (right). The phone next to the payment terminal is the attacker's card emulator device, and the phone next to the victim's card is the attacker's POS terminal emulator device. The attacker's devices communicate with each other via Wi-Fi, and with the terminal and card via NFC.
For the attacks to work, the criminals must have access to the victim's card, either by stealing it, finding it if lost, or holding a POS emulator next to it if the victim is still in possession of it. Attacks work by modifying terminal commands and card responses before delivering them to the appropriate recipient.
Our app does not require root privileges or any Android hacks. We used it on Google Pixel 2 XL and Huawei P Smart 2019 devices.
Attack on Visa The
attack consists in modifying the qualifiers of card transactions (CTQ, card data object) before they are delivered to the terminal. The modification tells the terminal that:
- PIN confirmation is not required, and
- The cardholder has been verified on the consumer's device (for example, a smartphone).
This attack can also affect Discover and UnionPay cards. Our findings were published by ETH Zurich , ACM TechNews , Schweizer Radio und Fernsehen (SRF) , The Hacker News , ZDNet , heise , and the full technical report is presented in our article:
EMV Standard: Hack, Fix, Verify
David Basin, Ralph Sasse and Jorge Toro-Pozo 42nd IEEE Security and Privacy Symposium (S&P) 2021
Mastercard Attack
This attack primarily involves replacing the legitimate application identifiers (AIDs) of the card with the Visa AID, A0000000031010, to force the terminal to activate the Visa core. The attacker then simultaneously performs a Visa transaction with a terminal and a Mastercard transaction with a card. In a Visa transaction, the attacker uses the aforementioned attack on Visa.
For this attack to work, the terminal authorization request must go to the issuing bank. Requirements for this include:
- the terminal does not refuse offline, even if the card number (PAN) and AID indicate different card brands, and
- The merchant's acquirer sends a transaction authorization request to a payment network that can process Mastercard cards.
This attack can also affect JCB and American Express cards. Our research was published by ETH Zurich , ACM TechNews , The Hacker News , and a full technical report is provided in our article:
Card Brand Mixing Attack: Bypassing PIN in Non-Visa Cards by Using It for Visa Transactions
David Basin. Ralph Sasse and Jorge Toro-Pozo 30th USENIX Security Symposium 2021
Frequently Asked Questions
What cards are affected by these attacks?
We have successfully bypassed the PIN for Visa Credit, Visa Debit, Visa Electron, V Pay, Mastercard Credit and Maestro. Other EMV cards may be affected, but we have no real-world proof of this.
Have there been any reactions from the affected companies?
We have uncovered attacks on both Visa and Mastercard. As a result of our successful Mastercard disclosure process, the payment network has since implemented and deployed defense mechanisms against an attack affecting their cards.
What role did Tamarin play in this study?
Tamarin is a modern verification tool. With its help, we analyzed the full flow of EMV transaction execution with an unlimited number of executions executed simultaneously in a competitive environment, where all messages exchanged between the terminal and the card can be read / blocked / entered. The result of this analysis was the identification of new attacks that we are talking about, as well as the re-detection of existing ones. We also used Tamarin to design and test (under all the adversarial conditions described above) against all attacks.
There used to be many attacks on EMV, how are they different?
The previously reported practical attacks are either conspicuous and therefore difficult to use in practice, or they do not appear to be profitable to criminals due to the fact that they are only possible for inexpensive purchases. Our attacks allow attackers to execute high-value fraudulent transactions using an app that looks just like a commercial payment app such as Apple Pay or Google Pay to avoid detection.
Something went wrong? How can you avoid similar problems in the future?
Important data sent by the card during a transaction is not authenticated. Complex systems such as EMV must be analyzed by automated tools such as model validators. Humans cannot handle the volume of execution and branching phases that a complex system has, so security breaches are often overlooked.
Should our cards be protected in a “metal wallet” to prevent them from being read off remotely?
This can help. Although you still have problems if lost or stolen.
What actions should I take as a citizen now to protect myself?
Bank-recommended protection measures are applied. Block the card immediately after you realize that it is lost or stolen. Check your bank statement regularly and report back to your bank immediately when you see an unrecognized transaction. Also, whenever you carry a contactless EMV card, make sure no one is holding the device next to it against your will. Also be mindful of your back pocket



















