Today, everyone has a computer, phone, tablet and other digital media, from small to large. It is not surprising that, as is the case with everything in our life, they are used not only to create what is reasonable, good, and eternal, but also to do things that are not quite right and good. In the case of illegal use of a digital device, or when an attacker used such a device to prepare or commit a crime, the data on the device can serve as proof of their guilt - the so-called digital proof.
Disappearing evidence
What happens when a working computer is found at a crime scene? In most cases, the investigator will simply turn it off. In the future, this computer will be studied by an expert in the study of computer information, and not by an investigator at all. All that will remain "in the hands" of the expert is the hard disk. Unfortunately, with this approach, access to a huge amount of "ephemeral" evidence is permanently lost, irrevocably disappearing when the power is turned off. These clues are data stored in RAM.
By turning off the computer without first taking a snapshot of the RAM, investigative authorities may never see the latest messages sent to suspects via social networks. Keys that can be used to encrypt cryptographic containers will be lost. If the "privacy" mode was used, the expert Advisor will never see the sites that were open when the power was turned off. Many other data will also be permanently lost.
All you need to do in order not to lose these and many other clues is to save the RAM image to a file.
What you can find in RAM
If you search carefully, you can find the most unexpected things in the computer's RAM. For example, keys that can be used to instantly decrypt the contents of the TrueCrypt, BitLocker, and PGP Disk cryptographic containers. This feature is available, for example, in the Russian-developed program Elcomsoft Forensic Disk Decryptor. But an attack on encrypted data "head-on" will take billions of years - after all, professionals in their field have worked for many years, trying to protect themselves primarily from brute-force attacks.
The RAM contains the latest messages received and sent via social networks; comments left on forums; messages transmitted using instant messaging programs or using chats built into electronic games. There you can find information about the last downloaded files. Pages and images from websites are stored in the computer's memory for some time - even if the browser has privacy protection mode enabled, cache is disabled, and session history is saved.
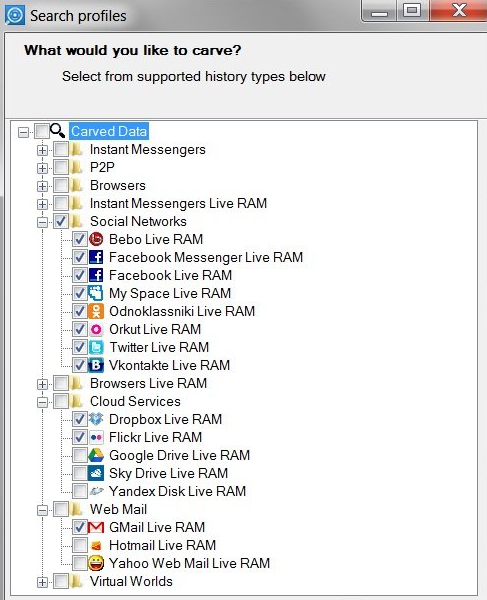
What can be" extracted " from RAM
How to remove a memory image
Saving the contents of the computer's RAM for later study is a necessary step in the work of a" digital " criminologist. Creating a memory image takes minutes, and with the proper level of technical support, it is done with a single button. At the same time, the "proper level of technical support" stands for very simple: just any USB flash drive that can fully accommodate the contents of RAM, and a small program-for example, the free utility of the Russian development Belkasoft Live RAM Capturer.
When removing the RAM image, the investigator needs to take into account a number of subtleties. For example, you can't use programs running in normal user mode to do this, and here's why.
Many programs, including popular multiplayer games, security systems, and malware, protect their processes from investigation by using debugging tools (for example, the Karos game). These programs use active anti-debugging systems that can detect and prevent other programs from trying to read data from protected memory areas. At best, an attempt to use the debugger fails - instead of the information that the researcher is interested in, zeros or random data are found in the protected area.
Therefore, running a utility that works in user mode is likely to cause the data that the expert is interested in to be unable to be extracted, and in the worst case scenario, they will be permanently destroyed. To prevent such a situation, criminologists have to use specialized programs and tools for example, CaptureGUARD Gateway, WindowsSCOPE worth about five thousand dollars, or the free Belkasoft Live RAM Capturer.
Many paid (and very expensive) forensic products (mostly of foreign production) include programs that allow you to take memory casts. At the same time, such programs operate in user mode and are completely unsuitable for real use by a criminologist. During forensic conferences, the question often arises: why do manufacturers of expensive analytical packages supply obviously inoperable tools? Manufacturers remain silent.
But the already mentioned Live RAM Capturer of the Russian company Belkasoft does not cost a penny, but it does all the necessary work in kernel mode. You can download it from the official website - belkasoft.com
Capture a RAM impression - Belkasoft Live RAM Capturer
And if the computer is password-protected?
It is easy to remove a memory image if access to the computer is open or if the criminologist knows the password for any valid account. But what if access to the computer is blocked by an unknown password, and there is not enough time to crack it? In this case, the method described by Austrian researchers comes to the expert's aid. Let's digress for a moment from the investigation of crimes and look in the direction of iron. Most modern computers have one or more IEEE 1394 ports, also known as FireWire or i.LINK.
So, if the suspect's computer is locked with a password, and the criminologist needs to remove the RAM image, the criminologist connects his own computer to the suspect's computer using the most common FireWire cable. A program runs on the criminalist's computer (the simplest samples, for example, Inception or pyfw, written in Python, are publicly available; however, criminalists use more advanced software), with which all the contents of the RAM of the machine under investigation are downloaded to the investigator's computer.
What if the suspect's computer doesn't have a FireWire port? In this case, the criminologist can use their own adapter card. If you choose a fairly common model, the system will load the appropriate drivers automatically. Unfortunately, only an adapter with the PCMCIA, CardBus, or ExpressCard interface will provide correct operation, since only these interfaces provide direct access to the computer's memory. Adapters that work via USB do not have this feature and are unsuitable for a criminologist.
Is there any protection against FireWire attacks? There are ways to protect yourself from such an attack, and they have long been known: you only need to disable FireWire support in one way or another while the computer is "sleeping" or closed with a password. Computers running the latest versions of OS X do this automatically by blocking FireWire drivers until the user logs in with their username and password. But in Windows and other operating systems, the situation is reversed: manufacturers of these systems do not block the operation of FireWire drivers.
Limitations
RAM analysis is not a panacea. The nature of RAM is such that data is stored in it only for a very short time. After a few minutes, or in extreme cases, hours (if the computer was not used), the data may be pushed out or overwritten with other information. Therefore, you need to take a memory impression "in fresh footsteps". But with the analysis of the captured image, you can take your time the file from the flash drive will not go anywhere.
What's next? Analyzing the contents of RAM
The RAM image is removed. What's next? The memory image obtained with the right tool can be analyzed by one of the specialized forensic products. Studying the computer RAM image allows forensic scientists to detect data that does not end up on the hard drive, such as chat conversations, social media and games, images, browser history, registry data, conversations in online multiplayer games, and much more.
The tools are selected by the expert depending on what exactly you want to detect. Unfortunately, today there is no universal solution. Some programs allow you to extract keys that can be used to decrypt cryptographic containers. Others allow you to find messages sent by the computer user via social networks, mail, or instant messaging programs.
There are tools for reconstructing the analysis of images viewed by the suspect (by the way, at least one pedophile who was released after a significant period of time was exposed using such a tool. The same tool helped exonerate a suspect who was slandered by his wife during the divorce process). Finally, there are programs that can be used to restore information about network connections that were active when the image was removed.
Search and analyze photos
When conducting investigations related to sexual crimes, it is important for the investigator to find out what images (photos) the suspect viewed. Studying the hard disk does not always help: the section of interest to the investigator may be encrypted, and the browser may have "privacy" mode enabled (or" incognito " according to Chrome). The essence of these modes is the same in all browsers: no information about user actions on the Internet gets to the hard disk. Accordingly, when you turn off the computer (or close the browser), all data is lost.
Nevertheless, this data is still stored somewhere, and in this situation, analyzing the RAM impression can also help. Images are searched using the signature search method. This mechanism is very similar to how antivirus programs work: to search for images, a set of signatures that occur in a particular graphic format is used. For example, the JFIF signature is found at the beginning of all JPEG files. After detecting the signature, the algorithm analyzes neighboring bytes of data.
Does it look simple? Indeed, it is not difficult to implement such an algorithm, and it is used by the vast majority of developers of forensic programs. But here there is not just a pitfall, but a whole huge underwater reef. The fact is that Windows does not always store large amounts of data in a continuous sequence. Instead, the operating system writes data to any free memory pages and it is far from certain that these pages will be arranged sequentially.
To help the criminologist comes a set of heuristic algorithms that collect photos from many small fragments according to the mosaic principle. Such algorithms are implemented in the domestic forensic package Belkasoft Evidence Center, and the complexity of their implementation is such that there are simply no alternatives at the moment. The result is not always guaranteed here, and such algorithms work dozens of times slower than the usual signature search. However, the result is worth it — after all, cheap machine time is spent, and not the manual work of an expert.
Programs for finding clues in your computer's memory
Experts use the following basic programs to analyze RAM:
Belkasoft Evidence Center www.belkasoft.com -search for chats, posts, and comments social networks; messages sent through numerous instant messaging programs, and many other types of evidence. Russian development;
Elcomsoft Forensic Disk Decryptor www.elcomsoft.com - a tool that allows you to instantly decrypt the contents of TrueCrypt, BitLocker, and PGP Disk cryptographic containers. Also a Russian development;
Passware Kit Forensic www.passware.com - a tool that allows you to instantly decrypt the contents of TrueCrypt, BitLocker, and PGP Disk cryptographic containers. It can capture a memory image using a FireWire attack. Russian development;
Guidance EnCase www.guidancesoftware.com - the most powerful analytical package that allows you to collect and process many types of evidence. It is the de facto standard tool used by the American police. Developed in the USA.
Paperwork
The work of a forensic expert consists only in a small part of the search and analysis of evidence. A significant part of the time is spent documenting the process: this is necessary so that the evidence found can be presented in court as physical evidence.
In order for the collected evidence to turn into a solid evidence base, the expert must not only document each step in detail, but also be ready to speak in court, proving the validity of using certain methods and tools.
Using programs to remove a RAM image inevitably leaves traces in the computer's memory. The program itself takes up space in memory, and if this is the case, some of the original data will be pushed out (overwritten). Therefore, you need to use a program with a minimum amount of RAM occupied, and the fact of partial rewriting of content must be carefully documented. More recently, the courts refused to accept as material evidence data that was changed in the process of obtaining them.
Analyze a running computer or examine the contents of a hard disk?
As mentioned above, the analysis of a running machine inevitably affects the contents of RAM. In many cases, the data stored on the hard disk may also change. Nevertheless, in some cases, specialists are in no hurry to turn off the computer.
When do I need to analyze a running computer? As a rule, such an analysis is resorted to in cases where you do not expect to find significant evidence on the computer's hard disk, but the study of data available through network connections opened on the computer can bring significant dividends.
When the computer shuts down, access to external network resources and VPN sessions is lost. If the computer was used as a terminal, and the real data is stored somewhere on a remote server, the expert has to analyze the equipment live. This method of analysis involves a large number of risks, and it requires a highly qualified expert (and a court permit). Accordingly, they do not often resort to investigating a running computer.
Confiscate the computer
Let's put ourselves in the shoes of a forensic expert. If you have a working computer, we need to examine its contents. Our actions?
Until recently, the computer was turned off (often simply de-energized to prevent programs that clear log files at the end of a work session), after which all hard drives were removed from it, which were connected to a device that blocked write operations. Virtual images were taken from the disks, and the expert worked with them in a calm environment.
With the development of technology, this method has become obsolete. Here, for example, are the recommendations given by the official ACPO (Association of Chief Police Officers) instruction to British police officers:
Conduct a risk assessment. Is it necessary and possible to make a copy of ephemeral data?
If the option exists, install a device for making a RAM impression (flash drive, external disk, etc.).
Run the program to remove the memory image.
When the program is finished, stop the device correctly.
Eject the device used to remove the memory image.
Check that the saved image is correct (you must use the investigator's computer, not the computer that the expert analyzes).
After checking the removed image, immediately proceed to the computer shutdown procedure.
What you can learn about your phone by putting it in the freezer
A funny study was conducted by German scientists. When analyzing the RAM of a phone running the Android operating system, they used a household freezer (bit.ly/Xa9XXN).
The idea to freeze the phone is connected with the appearance of the ability to encrypt partitions in the Android 4.0 system. This feature does not allow the researcher to access the information recorded in the locked phone without entering the correct password. Since password selection is a long and thankless task, the researchers decided to look for a way to bypass the protection.
In the same way as in the already familiar cryptographic containers, keys for decrypting data recorded in the phone are stored in the device's RAM. If it were possible to extract these keys, researchers would be able to use them to decrypt the contents of the device.
There is a possibility to remove an image of the RAM of an Android device: to do this, the phone is switched to a special fastboot debugging mode; a special program is installed in the memory, and the RAM image can be downloaded via USB. The problem here is that when you restart the phone in debugging mode, the contents of RAM have time to reset to zero.
To slow down the process of zeroing out the memory, scientists put the phone in the freezer, freezing it to a temperature of -15 degrees. At such a low temperature, the memory cells change state very slowly. Accordingly, when you turn off the cooled phone and immediately restart it in debugging mode, the contents of RAM do not have time to reset to zero. The experiment turned out to be successful: the researchers managed to extract binary keys from the phone, which were used to encrypt sections with user data.
More information about this experiment can be found on the university's website. The FROST software package is also available there, which is used to download a RAM image and extract crypto keys: bit.ly/Xa9XXN
Conclusion
The work of a "digital" criminologist is interesting and unusual. Qualified experts are always lacking everywhere. At an American conference, the chief of the city police department complained about the tight schedule of computer criminologists: an expert can spend no more than forty minutes examining each confiscated device. What can you do in forty minutes? Using the programs described in this article - very, very much.
Disappearing evidence
What happens when a working computer is found at a crime scene? In most cases, the investigator will simply turn it off. In the future, this computer will be studied by an expert in the study of computer information, and not by an investigator at all. All that will remain "in the hands" of the expert is the hard disk. Unfortunately, with this approach, access to a huge amount of "ephemeral" evidence is permanently lost, irrevocably disappearing when the power is turned off. These clues are data stored in RAM.
By turning off the computer without first taking a snapshot of the RAM, investigative authorities may never see the latest messages sent to suspects via social networks. Keys that can be used to encrypt cryptographic containers will be lost. If the "privacy" mode was used, the expert Advisor will never see the sites that were open when the power was turned off. Many other data will also be permanently lost.
All you need to do in order not to lose these and many other clues is to save the RAM image to a file.
What you can find in RAM
If you search carefully, you can find the most unexpected things in the computer's RAM. For example, keys that can be used to instantly decrypt the contents of the TrueCrypt, BitLocker, and PGP Disk cryptographic containers. This feature is available, for example, in the Russian-developed program Elcomsoft Forensic Disk Decryptor. But an attack on encrypted data "head-on" will take billions of years - after all, professionals in their field have worked for many years, trying to protect themselves primarily from brute-force attacks.
The RAM contains the latest messages received and sent via social networks; comments left on forums; messages transmitted using instant messaging programs or using chats built into electronic games. There you can find information about the last downloaded files. Pages and images from websites are stored in the computer's memory for some time - even if the browser has privacy protection mode enabled, cache is disabled, and session history is saved.

What can be" extracted " from RAM
How to remove a memory image
Saving the contents of the computer's RAM for later study is a necessary step in the work of a" digital " criminologist. Creating a memory image takes minutes, and with the proper level of technical support, it is done with a single button. At the same time, the "proper level of technical support" stands for very simple: just any USB flash drive that can fully accommodate the contents of RAM, and a small program-for example, the free utility of the Russian development Belkasoft Live RAM Capturer.
When removing the RAM image, the investigator needs to take into account a number of subtleties. For example, you can't use programs running in normal user mode to do this, and here's why.
Many programs, including popular multiplayer games, security systems, and malware, protect their processes from investigation by using debugging tools (for example, the Karos game). These programs use active anti-debugging systems that can detect and prevent other programs from trying to read data from protected memory areas. At best, an attempt to use the debugger fails - instead of the information that the researcher is interested in, zeros or random data are found in the protected area.
Therefore, running a utility that works in user mode is likely to cause the data that the expert is interested in to be unable to be extracted, and in the worst case scenario, they will be permanently destroyed. To prevent such a situation, criminologists have to use specialized programs and tools for example, CaptureGUARD Gateway, WindowsSCOPE worth about five thousand dollars, or the free Belkasoft Live RAM Capturer.
Many paid (and very expensive) forensic products (mostly of foreign production) include programs that allow you to take memory casts. At the same time, such programs operate in user mode and are completely unsuitable for real use by a criminologist. During forensic conferences, the question often arises: why do manufacturers of expensive analytical packages supply obviously inoperable tools? Manufacturers remain silent.
But the already mentioned Live RAM Capturer of the Russian company Belkasoft does not cost a penny, but it does all the necessary work in kernel mode. You can download it from the official website - belkasoft.com
Capture a RAM impression - Belkasoft Live RAM Capturer
And if the computer is password-protected?
It is easy to remove a memory image if access to the computer is open or if the criminologist knows the password for any valid account. But what if access to the computer is blocked by an unknown password, and there is not enough time to crack it? In this case, the method described by Austrian researchers comes to the expert's aid. Let's digress for a moment from the investigation of crimes and look in the direction of iron. Most modern computers have one or more IEEE 1394 ports, also known as FireWire or i.LINK.
So, if the suspect's computer is locked with a password, and the criminologist needs to remove the RAM image, the criminologist connects his own computer to the suspect's computer using the most common FireWire cable. A program runs on the criminalist's computer (the simplest samples, for example, Inception or pyfw, written in Python, are publicly available; however, criminalists use more advanced software), with which all the contents of the RAM of the machine under investigation are downloaded to the investigator's computer.
What if the suspect's computer doesn't have a FireWire port? In this case, the criminologist can use their own adapter card. If you choose a fairly common model, the system will load the appropriate drivers automatically. Unfortunately, only an adapter with the PCMCIA, CardBus, or ExpressCard interface will provide correct operation, since only these interfaces provide direct access to the computer's memory. Adapters that work via USB do not have this feature and are unsuitable for a criminologist.
Is there any protection against FireWire attacks? There are ways to protect yourself from such an attack, and they have long been known: you only need to disable FireWire support in one way or another while the computer is "sleeping" or closed with a password. Computers running the latest versions of OS X do this automatically by blocking FireWire drivers until the user logs in with their username and password. But in Windows and other operating systems, the situation is reversed: manufacturers of these systems do not block the operation of FireWire drivers.
Limitations
RAM analysis is not a panacea. The nature of RAM is such that data is stored in it only for a very short time. After a few minutes, or in extreme cases, hours (if the computer was not used), the data may be pushed out or overwritten with other information. Therefore, you need to take a memory impression "in fresh footsteps". But with the analysis of the captured image, you can take your time the file from the flash drive will not go anywhere.
What's next? Analyzing the contents of RAM
The RAM image is removed. What's next? The memory image obtained with the right tool can be analyzed by one of the specialized forensic products. Studying the computer RAM image allows forensic scientists to detect data that does not end up on the hard drive, such as chat conversations, social media and games, images, browser history, registry data, conversations in online multiplayer games, and much more.
The tools are selected by the expert depending on what exactly you want to detect. Unfortunately, today there is no universal solution. Some programs allow you to extract keys that can be used to decrypt cryptographic containers. Others allow you to find messages sent by the computer user via social networks, mail, or instant messaging programs.
There are tools for reconstructing the analysis of images viewed by the suspect (by the way, at least one pedophile who was released after a significant period of time was exposed using such a tool. The same tool helped exonerate a suspect who was slandered by his wife during the divorce process). Finally, there are programs that can be used to restore information about network connections that were active when the image was removed.
Search and analyze photos
When conducting investigations related to sexual crimes, it is important for the investigator to find out what images (photos) the suspect viewed. Studying the hard disk does not always help: the section of interest to the investigator may be encrypted, and the browser may have "privacy" mode enabled (or" incognito " according to Chrome). The essence of these modes is the same in all browsers: no information about user actions on the Internet gets to the hard disk. Accordingly, when you turn off the computer (or close the browser), all data is lost.
Nevertheless, this data is still stored somewhere, and in this situation, analyzing the RAM impression can also help. Images are searched using the signature search method. This mechanism is very similar to how antivirus programs work: to search for images, a set of signatures that occur in a particular graphic format is used. For example, the JFIF signature is found at the beginning of all JPEG files. After detecting the signature, the algorithm analyzes neighboring bytes of data.
Does it look simple? Indeed, it is not difficult to implement such an algorithm, and it is used by the vast majority of developers of forensic programs. But here there is not just a pitfall, but a whole huge underwater reef. The fact is that Windows does not always store large amounts of data in a continuous sequence. Instead, the operating system writes data to any free memory pages and it is far from certain that these pages will be arranged sequentially.
To help the criminologist comes a set of heuristic algorithms that collect photos from many small fragments according to the mosaic principle. Such algorithms are implemented in the domestic forensic package Belkasoft Evidence Center, and the complexity of their implementation is such that there are simply no alternatives at the moment. The result is not always guaranteed here, and such algorithms work dozens of times slower than the usual signature search. However, the result is worth it — after all, cheap machine time is spent, and not the manual work of an expert.
Programs for finding clues in your computer's memory
Experts use the following basic programs to analyze RAM:
Belkasoft Evidence Center www.belkasoft.com -search for chats, posts, and comments social networks; messages sent through numerous instant messaging programs, and many other types of evidence. Russian development;
Elcomsoft Forensic Disk Decryptor www.elcomsoft.com - a tool that allows you to instantly decrypt the contents of TrueCrypt, BitLocker, and PGP Disk cryptographic containers. Also a Russian development;
Passware Kit Forensic www.passware.com - a tool that allows you to instantly decrypt the contents of TrueCrypt, BitLocker, and PGP Disk cryptographic containers. It can capture a memory image using a FireWire attack. Russian development;
Guidance EnCase www.guidancesoftware.com - the most powerful analytical package that allows you to collect and process many types of evidence. It is the de facto standard tool used by the American police. Developed in the USA.
Paperwork
The work of a forensic expert consists only in a small part of the search and analysis of evidence. A significant part of the time is spent documenting the process: this is necessary so that the evidence found can be presented in court as physical evidence.
In order for the collected evidence to turn into a solid evidence base, the expert must not only document each step in detail, but also be ready to speak in court, proving the validity of using certain methods and tools.
Using programs to remove a RAM image inevitably leaves traces in the computer's memory. The program itself takes up space in memory, and if this is the case, some of the original data will be pushed out (overwritten). Therefore, you need to use a program with a minimum amount of RAM occupied, and the fact of partial rewriting of content must be carefully documented. More recently, the courts refused to accept as material evidence data that was changed in the process of obtaining them.
Analyze a running computer or examine the contents of a hard disk?
As mentioned above, the analysis of a running machine inevitably affects the contents of RAM. In many cases, the data stored on the hard disk may also change. Nevertheless, in some cases, specialists are in no hurry to turn off the computer.
When do I need to analyze a running computer? As a rule, such an analysis is resorted to in cases where you do not expect to find significant evidence on the computer's hard disk, but the study of data available through network connections opened on the computer can bring significant dividends.
When the computer shuts down, access to external network resources and VPN sessions is lost. If the computer was used as a terminal, and the real data is stored somewhere on a remote server, the expert has to analyze the equipment live. This method of analysis involves a large number of risks, and it requires a highly qualified expert (and a court permit). Accordingly, they do not often resort to investigating a running computer.
Confiscate the computer
Let's put ourselves in the shoes of a forensic expert. If you have a working computer, we need to examine its contents. Our actions?
Until recently, the computer was turned off (often simply de-energized to prevent programs that clear log files at the end of a work session), after which all hard drives were removed from it, which were connected to a device that blocked write operations. Virtual images were taken from the disks, and the expert worked with them in a calm environment.
With the development of technology, this method has become obsolete. Here, for example, are the recommendations given by the official ACPO (Association of Chief Police Officers) instruction to British police officers:
Conduct a risk assessment. Is it necessary and possible to make a copy of ephemeral data?
If the option exists, install a device for making a RAM impression (flash drive, external disk, etc.).
Run the program to remove the memory image.
When the program is finished, stop the device correctly.
Eject the device used to remove the memory image.
Check that the saved image is correct (you must use the investigator's computer, not the computer that the expert analyzes).
After checking the removed image, immediately proceed to the computer shutdown procedure.
What you can learn about your phone by putting it in the freezer
A funny study was conducted by German scientists. When analyzing the RAM of a phone running the Android operating system, they used a household freezer (bit.ly/Xa9XXN).
The idea to freeze the phone is connected with the appearance of the ability to encrypt partitions in the Android 4.0 system. This feature does not allow the researcher to access the information recorded in the locked phone without entering the correct password. Since password selection is a long and thankless task, the researchers decided to look for a way to bypass the protection.
In the same way as in the already familiar cryptographic containers, keys for decrypting data recorded in the phone are stored in the device's RAM. If it were possible to extract these keys, researchers would be able to use them to decrypt the contents of the device.
There is a possibility to remove an image of the RAM of an Android device: to do this, the phone is switched to a special fastboot debugging mode; a special program is installed in the memory, and the RAM image can be downloaded via USB. The problem here is that when you restart the phone in debugging mode, the contents of RAM have time to reset to zero.
To slow down the process of zeroing out the memory, scientists put the phone in the freezer, freezing it to a temperature of -15 degrees. At such a low temperature, the memory cells change state very slowly. Accordingly, when you turn off the cooled phone and immediately restart it in debugging mode, the contents of RAM do not have time to reset to zero. The experiment turned out to be successful: the researchers managed to extract binary keys from the phone, which were used to encrypt sections with user data.
More information about this experiment can be found on the university's website. The FROST software package is also available there, which is used to download a RAM image and extract crypto keys: bit.ly/Xa9XXN
Conclusion
The work of a "digital" criminologist is interesting and unusual. Qualified experts are always lacking everywhere. At an American conference, the chief of the city police department complained about the tight schedule of computer criminologists: an expert can spend no more than forty minutes examining each confiscated device. What can you do in forty minutes? Using the programs described in this article - very, very much.



















